Highlighting Data Protection Best Practices for IIoT Systems
| Contact Us | |
| Free Demo | |
| Chat | |
As IIoT (Industrial IoT) systems continue to interact with enterprise systems and business processes, a new guide offers a set of best practices to securing them.
In so-called smart factories today, sensors, instruments, and other devices must work together in concert to achieve an objective. Whether it’s manufacturing tiny batteries, sensors for cars, or, light railways, factories have embraced the industrial internet of things (IIoT) to measure data in order to better facilitate automation.
As with any highly technical environment, protecting data as it makes its way through these increasingly complex ecosystems is paramount.
Not only does data protection ensure compliance in these environments, it helps safeguard intellectual property and protects against data leaks.
While there’s no shortage of guidance on securing internet of things devices, one group, The Industrial Internet Consortium, a non-profit, has made it its objective to foster trustworthiness and security in Industrial Internet of Things environments specifically. The Massachusetts-based consortium, which was formed in 2014, counts GE, Microsoft, and Dell EMC among some of its founding and contributing members.
The group released a new guide around data protection best practices this week. In it, the group breaks down some of the consequences for failing to apply proper data protection to IIoT systems and the steps the IIS recommends organizations take around cryptography, encryption, auditing, monitoring, and protecting data.
The best practices help inform the IIC's IoT Trustworthiness framework, a framework that's rooted in the idea that data security should help inform the privacy, reliability, resilience, and safety of IoT systems.
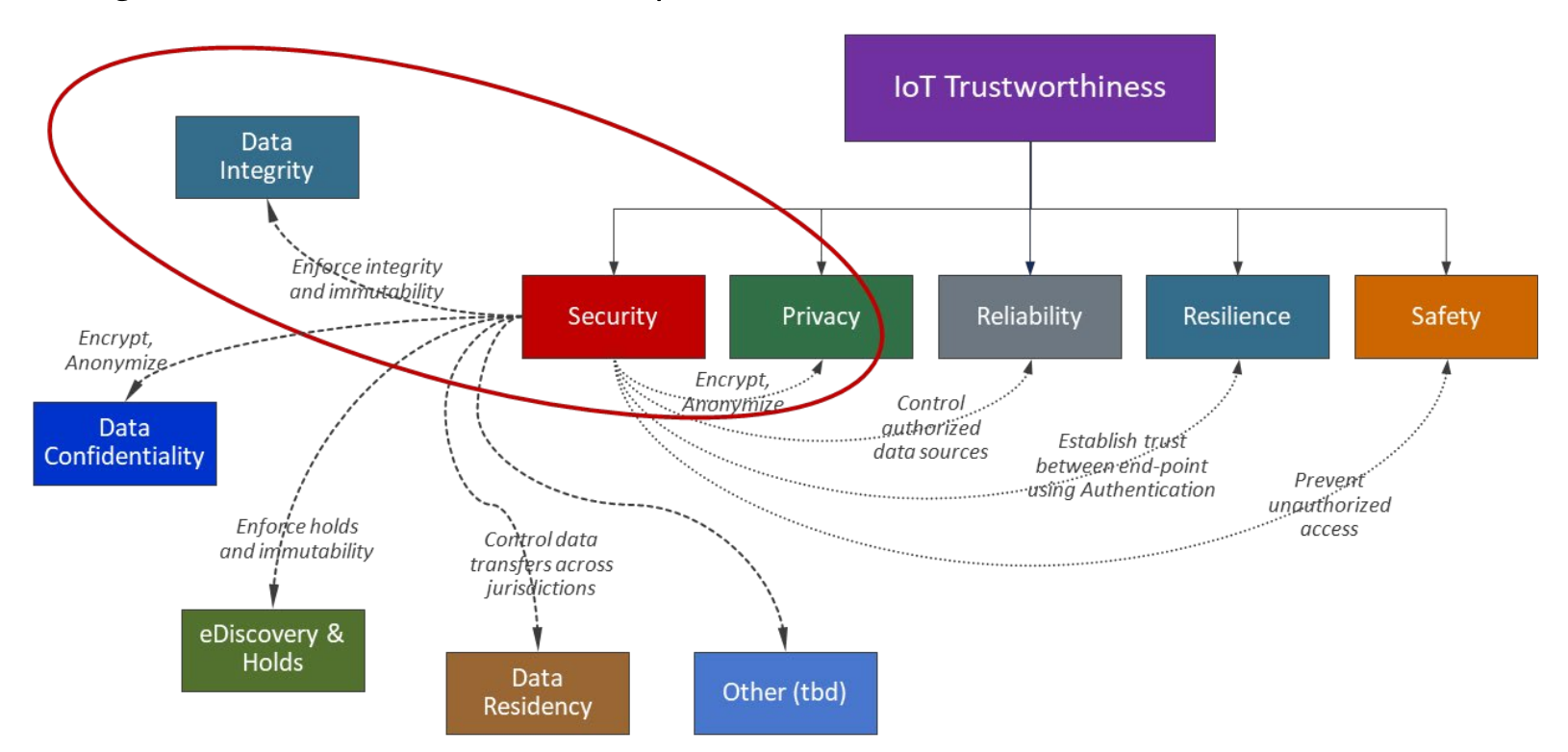
The paper also digs into data security concepts, like data integrity, data confidentiality, data residency, how they apply to data - at rest, in motion, and in use – and how specifically they relate to IoT data. For instance, the paper warns against over retaining IoT data, something that can open the door to legal and regulatory risks. Like any form of sensitive data, the IIC's best practices advise protecting and safeguarding the integrity of IoT data as well.
The group notes in the paper that the best practices are designed to help complement additional sector-specific guidance, like its IoT Security Maturity Model (IISM) and parts of its Industrial Internet Reference Architecture (IIRA) and Industrial Internet Security Framework (IISF). The group notes that insight from other, non-IIS frameworks, helped inform the paper, including IEC 62443, IEC 61508, and CSA CCM.
As Internet of Things technology has blossomed over the last several years, the manufacturing and industrial sector, namely Industrial Automation and Control Systems (IACS) have adapted, with many organizations electing to deploy IoT technology to bridge the gap between connectivity and industrial systems.
IIoT usage isn’t widespread yet – in a recent survey, roughly half of businesses interviewed were either deploying or trialing IIoT solutions – but because it results in increased operational efficiency, it's expected to factor into the future of production systems.
The ability to identify and secure sensitive data across a complex supply chain is a necessity for any organization looking to mitigate risk while implementing a IIoT system.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.