The Evolution of DLP: 4 Reasons Why DLP is Back in the Limelight
| Contact Us | |
| Free Demo | |
| Chat | |
There are multiple trends driving a resurgence of interest in data loss prevention - let's look at four of them in part two of our Definitive Guide to DLP series.
Data loss prevention came to market with big interest and bigger expectations. Looking back a decade ago, the demand for DLP was primarily driven by data protection requirements for regulatory compliance, such as PCI, PII and HIPAA. Organizations later expanded DLP usage to protect intellectual property such as trade secrets, design documents, formulas, etc.
However, interest softened as organizations struggled with the cost and the complexity of deploying first generation DLP software. 2008 saw a dip in DLP deployments because many organizations found DLP solutions to be resource-intensive and required a steep learning curve.
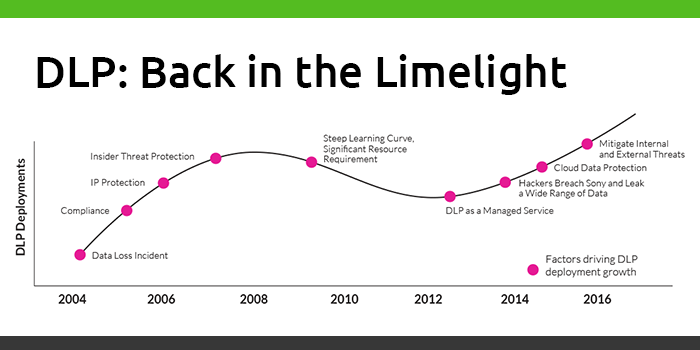
Despite increased awareness and more sophisticated security measures, the dramatic increase in data breaches has brought attention back to data protection technologies. The following four factors have pushed DLP in particular back into the limelight.
1. DLP as a service. DLP as a technology has made great strides and has matured enough to be deployed as a managed service. Selective DLP vendors have in-house security experts that live and breathe data protection every day, acting as an extension of the IT team and expertly developing, deploying, and managing DLP programs on behalf of enterprises that have more IP than IT.
2. The Sony Pictures breach expands the definition of sensitive data. The Sony Pictures breach in 2014 completely changed what companies thought of as sensitive data. The leaked emails had devastating effects on Sony as they contained high-stakes financial deals, creative disagreements and executive ties to political and military groups. The hack also exposed gender pay inequality issues in Hollywood that made headlines. As a result, the industry witnessed a major leap in terms of what constitutes sensitive data and expanded the definition of IP to include other types of data such as emails, processes, employee information, and the list keeps growing.
3. Cloud security concerns. In recent years, as enterprises move further along the cloud adoption curve, cloud storage security is becoming a top priority – both in enterprises’ IT architecture and information security strategies. Consequently, DLP technology has evolved to extend data protection policies in the cloud.
4. Extending DLP to advanced threat protection. In today’s massive interconnected world, companies are increasingly threatened by both insider threat actors and external threat actors. DLP solutions that can utilize the same endpoint agent to protect against advanced threats have dramatically increased the value of DLP.
To learn more about DLP and how it can help protect your organization from evolving threats, download the full guide.
Read more in our Definitive Guide to DLP Series
- Do you need DLP? Well, do you feel lucky?
- The Evolution of DLP: 4 Reasons Why DLP is Back in the Limelight
- Debunking the Three Myths of DLP
- Call it a Comeback: 7 Trends Driving the Resurgence of DLP
- All Trends Lead to Data-Centric Security
- What is Driving Your Data Protection Agenda? Determining the Right Approach to DLP
- Building a Value-Based Business Case for DLP
- Positioning DLP for Executive Buy-In
- 5 Criteria for Choosing the Right Managed Security Services Provider (MSSP)
- How to Evaluate DLP Solutions: 6 Steps to Follow and 10 Questions to Ask
- Getting Successful with DLP: Two Approaches for Quick DLP Wins
- Two Frameworks for DLP Success
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.