Insiders Responsible for 58 Percent of Healthcare Breaches
| Contact Us | |
| Free Demo | |
| Chat | |
58 percent of PHI data loss incidents from 2016 to 2017 involved internal actors according to Verizon's new Protected Health Information Data Breach Report.
When it comes to data incidents involving the healthcare industry ransomware is king but a recent report warns that facilities should never completely rule out the insider threat.
According to Verizon's Protected Health Information Data Breach Report (PHIDBR) – released late last week - more than half of healthcare sector incidents over the last two years involved insiders, attackers either looking to gain money by opening lines of credit with ill begotten information or nurses taking time out of their day to snoop on patients’ medical records.
Authors behind the report combed through 1,368 incidents included in both its 2016 and 2017 Data Breach Investigations Report (DBIR) for its findings.
Insiders at affected facilities caused 782 of the incidents, 57.5 percent but according to the report not all of the incidents were
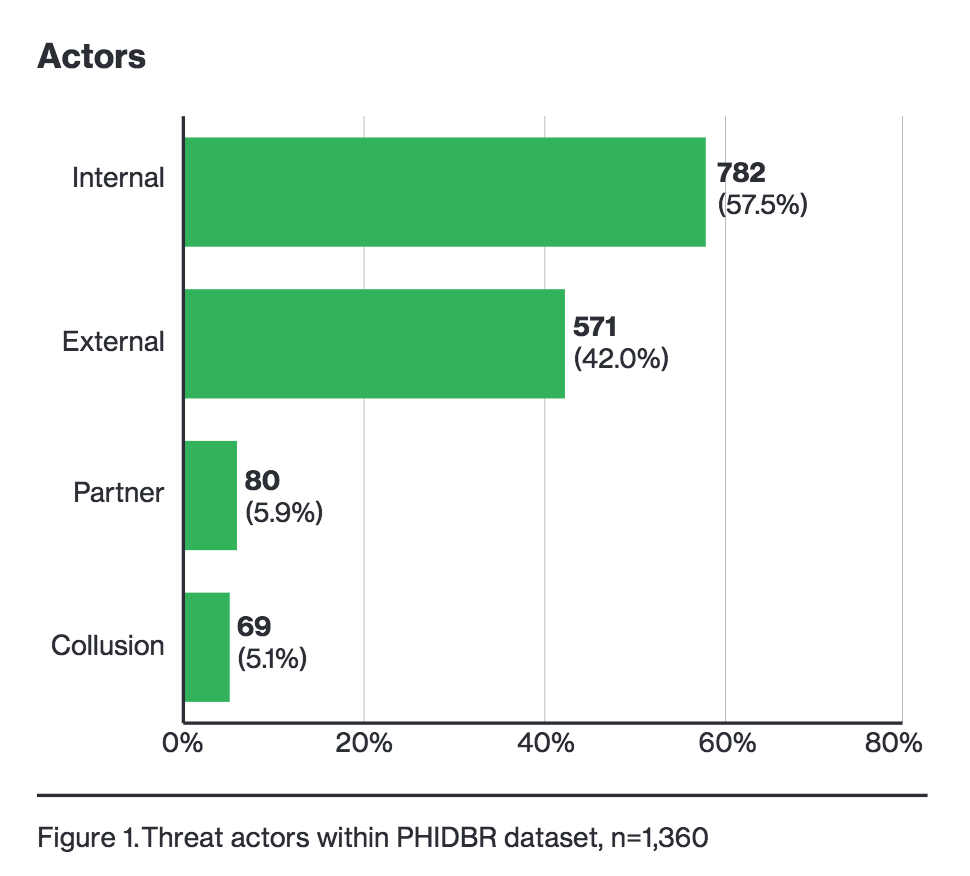
"Convenience as a motive comes into the picture when insiders do something that will make it easier for them to get their work done, but as a consequence also puts data at risk," the report reads. "An example would be violating data handling policies by storing sensitive data on unapproved hardware."
It should come as no surprise, especially given the recent rash of infections at hospitals nationwide, that ransomware attacks accounted for 70 percent of incidents involving malware in the report.
While just a handful of incidents involved point of sale RAM scraper malware, backdoors, or malicious spam, 91 of the incidents involved ransomware. Most of the ransomware targeted databases, servers, and desktops, some targeted file servers, end-users, and web apps, according to Verizon.
It's important to note that even incidents in which PHI or Protected Health Information was at risk but wasn't compromised is still considered a breach in the eyes of the report. The U.S. Department of Health and Human Services (HHS) issued guidance last year around ransomware attacks but in the end data breach notification requirements are ultimately triggered when there’s both unauthorized access to and acquisition of personally identifiable information (PII)
While all ransomware scenarios should technically be considered a breach, not all are reported. If an organization can establish that PHI was encrypted and wasn't compromised, they don't necessarily have to report it, as the data could be considered secure.
Verizon acknowledges in the report that while it includes data from incidents in 27 countries it leans mostly towards U.S. instances, largely due to the public access it and others are granted to records from the U.S. Health and Human Services and the Veterans Adminstration. The report aggregates statistics from across the healthcare sector: Doctor-owned clinics, large organizations, health insurance organizations, bill services, and courier services that handle PHI are all included.
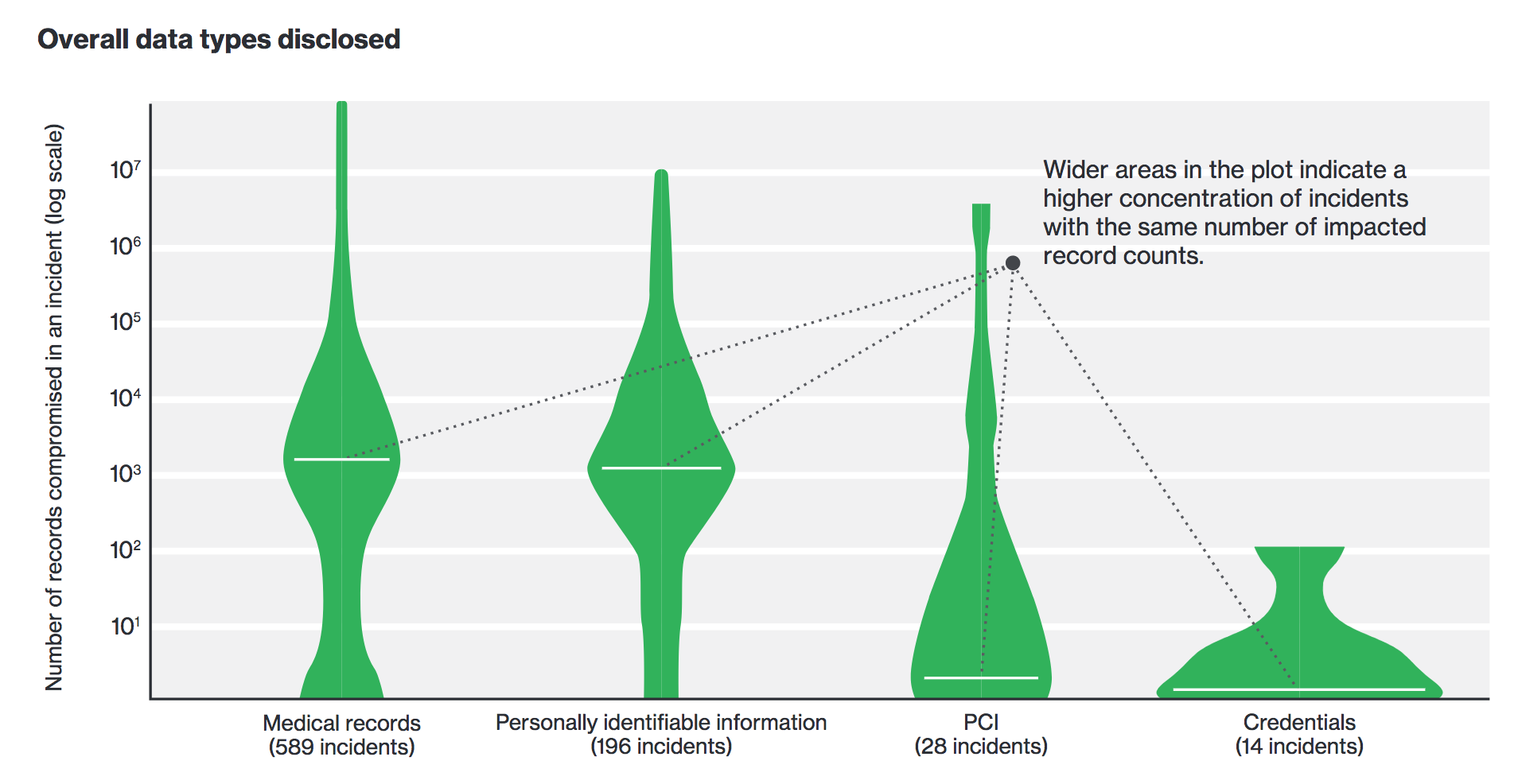
While there were more medical records stolen than PII, what's interesting is the concentration of incidents with the same number of impacted records. Looking at breaches within the PHI DBR dataset, medical records and PII are stolen in large fell swoops. In many instances credentials are being compromised one at a time, either via social engineering, information stealing malware, or other means, according to the report. PCI data meanwhile is being stolen in small quantities by insiders.
The report recommends healthcare facilities implement mitigations to thwart data leakage.
Hospitals and clinics should ensure data across all of its endpoints is protected by full disk encryption, put procedures and policies in place to monitor when internal PHI is accessed and do whatever they can to combat ransomware attacks.
"Our data shows that the most common vectors of malware are via email and malicious websites. Don’t allow a patient zero end-user device to easily propagate and spread ransomware to more critical assets and don’t use devices with high availability requirements to surf the internet or receive external email,” the report reads.
The report is the latest to delve into the number of healthcare breaches over the last several years. Last month the American Journal of Managed Care (AJMC) released a study that dug through 215 data breaches from 2009 to 2016. The report found that hospitals were the juiciest target for breaches: Nearly one third of incidents reported to HHS' Office for Civil Rights were hospital breaches.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.