Solving the Mid-Market Data Protection Challenge
| Contact Us | |
| Free Demo | |
| Chat | |
Learn how Digital Guardian's Managed Security Program for Midsize Companies can help organizations improve their information security program, whatever the use case.
If you’re a mid-market organization, you know about the challenge of competing against the resources of the big players while staying as nimble as the small players. Your information security program has these same constraints. While outsourcing your whole business is less of an option, outsourcing your information security can be one of the smartest decisions a mid-market security leader can make.
Digital Guardian announced a fully managed Data Loss Prevention (DLP) offering designed for the mid-market earlier this year. We looked at what our existing customers used as their most common data protection use cases and designed a program around that to provide a fully managed data protection solution that caters to the most common data protection needs.
When you subscribe to the Managed Security Program for Midsize Companies, you instantly gain access to a team of data security experts and a company with over 15 years’ experience implementing and improving mission-critical data visibility, IP protection, and compliance programs.
What are the specific use cases you get?
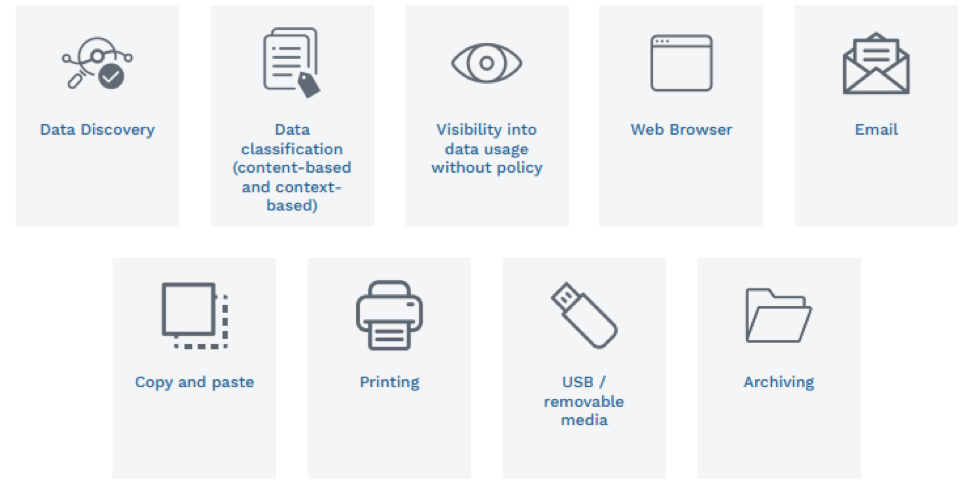
These nine data protection scenarios provide mid-market businesses with an effective information security program. In more detail, here’s a little more about each one.
1. Data Discovery – Before you can protect your data, you need to know where it is. Data discovery helps you inventory the data that lives within your business. Laptops, servers, network-attached storage, cloud, etc... we work with you to find the sensitive data important to your business.
2. Data classification – Next, through the application of data classification, your data is labeled to help drive data protection policies. Using a blend of content (what’s in the file, such as keywords, phrases, patterns, etc.) or context (attributes of the file like application, location, user, etc.) you get a more detailed understanding of what your data profile looks like. You can use that to focus your data protection program on what matters, like regulated data and intellectual property.
3. Visibility into data usage without policy – DG has the unique ability in the DLP market to deliver visibility into data movement without a policy to discover unknown data risks in your business.
4. Web Browser – Browsers and browser-based apps see tremendous use in business. Couple that with the frequency of browser updates, and the number of browsers, this channel presents great risk. DG gets you visibility and control of the data that flows via this channel.
5. Email – Perhaps the most commonly used (abused and misused) communication app. It provides the ability to instantly send the most sensitive company information to the wrong person. You can now see, alert, and even stop, in real time, sensitive materials from being emailed.
6. Copy and paste – One of the ways around file-based data protection is to simply copy/paste the relevant information into a new document. With Digital Guardian, the classification tags persist with the data, so when it gets pasted into a new document, the classification, and the associated protection, comes along too.
7. Printing – Printing often gets forgotten as a data egress/theft vector, and that is exactly why it needs to be protected. You can see everything that gets printed and add restrictions if desired. For example, any files from finance or engineering storage can only be printed to designated printers.
8. USB/removable media – USB devices (including connecting your phone) can be a great way to move large files but can also a risk. Once off the corporate map, infosec teams have no control of where it goes. With DG you have full visibility of any data that moves to a USB device, and you can add controls such as restricting movement only to registered USB devices or encrypting the data.
9. Archiving – Digital Guardian provides visibility into the archive activity at the time of archive (or changing the file name or extension) and maintains the data classification tag with the new archive file, ensuring the protection stays with your sensitive data.
Data protection use cases can vary widely, but when you apply the Pareto principle to them - for many outcomes, roughly 80% of consequences come from 20% of causes - a subset can deliver the most value, especially for mid-sized businesses that may struggle with an effective data protection program. Add in the expertise from a fully managed service and you have a simple, yet effective way to keep your regulated data and intellectual property under the control of the information security program.
To learn more about the Digital Guardian Managed Security Program for Midsize Companies, watch this video on the day in the life of a managed security program analyst to see what they do and how they can help your business grow, securely.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.