Data Protection – Are We Focused on the Correct Areas?
| Contact Us | |
| Free Demo | |
| Chat | |
How do you defend against data loss you can't see? The breaches you don't hear about? Our Wade Barisoff connects the dots between WWII airplanes and data protection to find the answer.
Lately, I’ve spent a lot of energy researching information available on data loss that’s been reported globally. There are plenty of official government sites that list data breach incidents, what occurred, what led to it, and recommended corrective actions to be taken.
Speaking of fixing things, I was recently reminded of a true World War II story about how the military tried to better armor their airplanes as the losses during the war mounted.
Back in 1999, I completed my pilot’s certificate and started to fly airplanes for fun. As a part of that community, people are always sharing stories and anecdotes that can remind us about our non-aviation lives. For me, that’s helping organizations stop data loss.
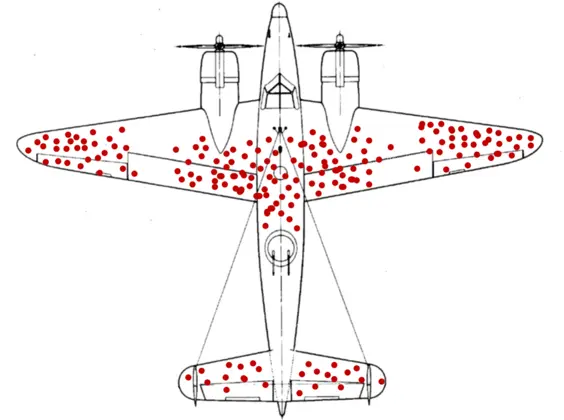
As the WWII story goes, after each plane returned from battle, it was mapped on the aircraft where the damage occurred. This data was collected and reported over time to the engineers, who used it to create a simple map that looked a lot like the following:
In looking at the holes in the returning aircraft, the military thought it knew where to reinforce their plane: the areas that were susceptible to enemy fire.
Statistician Abraham Wald argued however that the areas to reinforce were actually the nose, engines and mid-section, insisting the parts of the aircraft engineers needed to study were the ones that didn’t return from battle. This later became to be known as survivorship bias.
What does this have to do with data protection?
I was looking at the websites that detail reported breach events like engineers looked at data from aircraft that was returning from battle. What about the breaches we never hear about?
What about people that don’t report their mistakes because they don’t want to get into trouble? What about employees that send company property to personal mail accounts or file sharing sites? What about the individuals that send data to external sites for nefarious purposes like selling it for money or leaking company secrets?
These days, it seems like there’s a new way to share data every few weeks. As defenders, how do we solve for all these data sharing paths?
Roughly six years ago I was introduced to Digital Guardian Secure Collaboration
What impressed me at the time – even as new sharing methods were emerging – was that it was focused on the data and really didn’t care about where it was going. It didn’t care because as a solution it’s always focused on who has access to the information, not what repository the information is sitting in. Even if it was accidentally put in a public share of some form, you’d need to be granted rights to the file to see the information.
This is helpful in a lot of instances. If someone makes a mistake, like removing the rights of the person that received the file or if the person that received it never had rights in the first place. If someone sends company property home, either when leaving the company or prior to, you can remove their rights to that sensitive material too.
And that nefarious person? Anyone from the SOC can remove their rights. They can even track who opened the file with a neatly recorded chain of custody.
“Sounds like encryption, Wade”
Sure, but generally with encryption once the receiver has decrypted the file, they can do whatever they want; the toothpaste is out of the tube and there is no way to put it back. It checks permissions each time the file is opened, so if rights need to change, you can do it with immediate impact.
Our industry in general has deployed offenses for known issues but how can you look beyond what you know and best prepare for the unknown issues you may not have data on? How can you deploy a strategy for the data loss you never see?
Simple. Use a strategy including Digital Guardian Secure Collaboration that can not only show you but allow you to put additional security in areas that you didn’t realize were weak points.
Just like Abraham Wald and the military during World War II, are we solving for the right problem in the right way or just reacting to what we see? In the security industry we often refer to the unknown knowns. That’s where we can learn from Abraham.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.
Don't Fall Behind
Get the latest security insights
delivered to your inbox each week.
Thank you for subscribing!