Cyberespionage, Social Engineering, Misconfiguration Errors Culprits in Verizon's 2019 Data Breach Report
| Contact Us | |
| Free Demo | |
| Chat | |
The latest edition of the report analyzed over 40,000 security incidents to identify trends and changes by threat actors.
Cyberespionage, social engineering, and misconfiguration errors are increasingly to blame for security incidents, especially over the last year. The three attack patterns are just some of the more glaring issues outlined by Verizon's 2019 Data Breach Investigations Report, an annual recap of the threat landscape, at least from Verizon’s vantage, through the prism of thousands of security incidents.
This year’s report combed through 41,686 security incidents, 2,013 which were technically data breaches, from 73 data sources, the bulk of which are external to Verizon. The report classifies incidents as any event that compromises the integrity, confidentiality, or availability of an asset, it classifies a breach as any incident that results in the confirmed disclosure of data.
The leading cause of incidents and breaches in 2018? Denial of service attacks and phishing attacks still reign supreme.
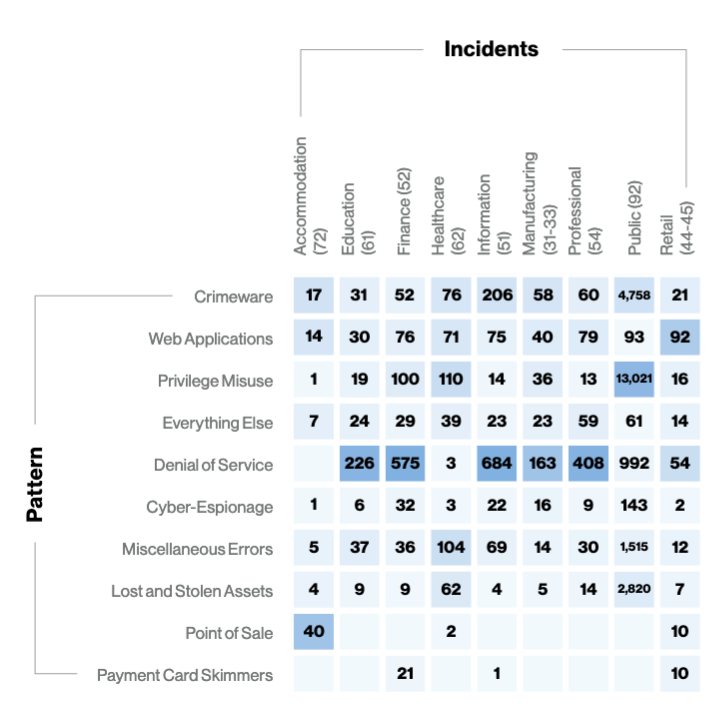
DOS attacks, especially in the finance, insurance and information sectors, remain a problem. DOS attacks were responsible for 63 percent of the incidents that hit the information sector and responsible for almost as many, over half of the incidents, to hit the educational sector.
This year's report warns that C-level executives, employees who often have readily available access to sensitive data, are 12 times more likely to be targeted by a social incident and nine times more likely to be the target of a social breach. The DBIR goes on to highlight a clear increase in the number of both incidents and breaches to affect execs, from single digits in the last report, to dozens this past year.
Phishing, which of course helps facilitate social engineering attacks, and credential theft of cloud-based mail accounts, were most prominent attack vectors in the professional, technical and scientific services sector. Verizon tallied 670 incidents in this sector, 157 which led to data disclosure.
According to the report, cyberespionage, the motive in 25 percent of the breaches looked at, is especially a problem in the public sector, where state-sponsored attackers are keen on securing access to networks and performing reconnaissance. The sector has seen perhaps the biggest uptick, a 168 percent increase, in the number of breaches over the last year, up from 25 percent in 2017 to 42 percent in 2018.
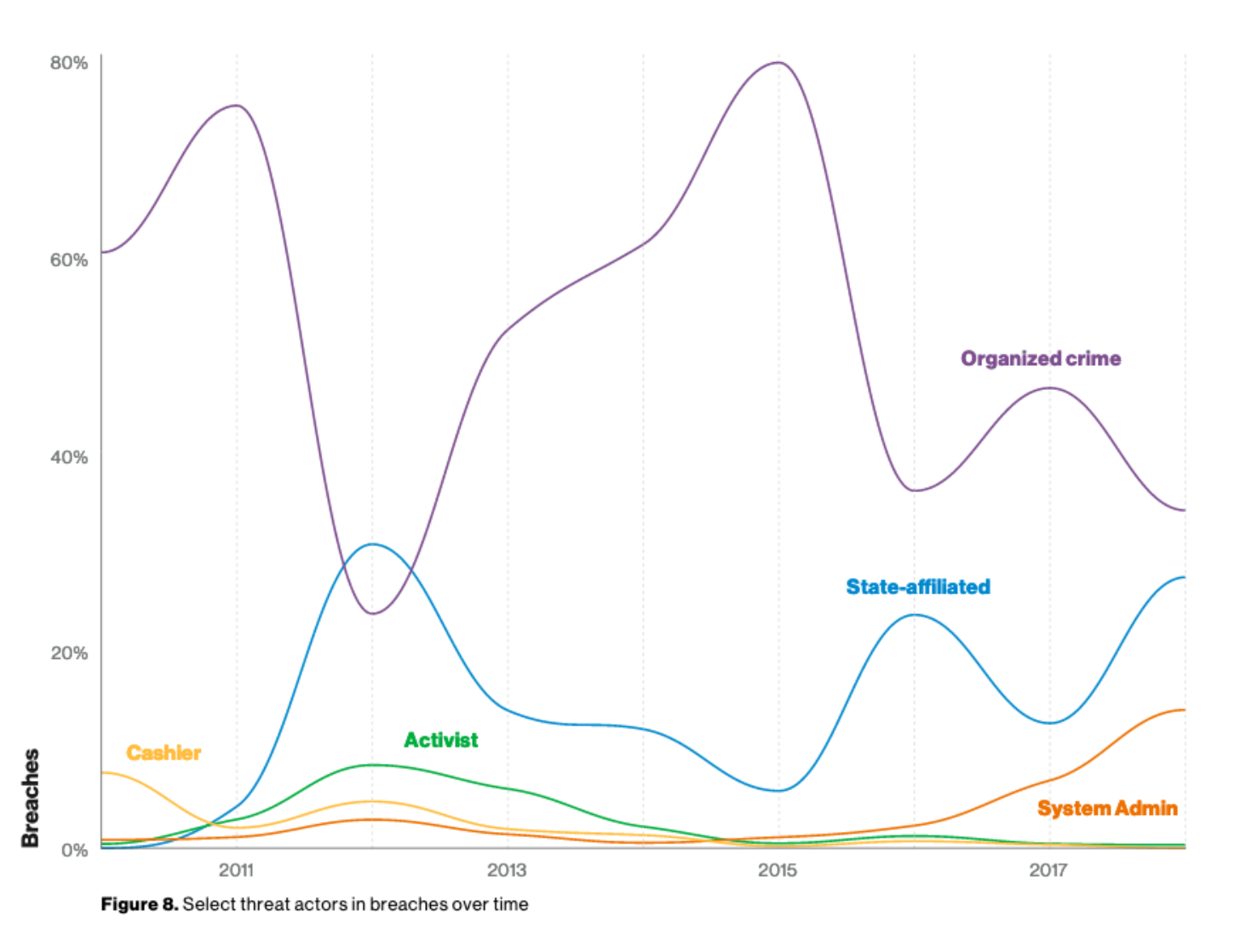
Collectively, cyberespionage, miscellaneous errors and privilege misuse accounted for 72 percent of breaches to government entities, according to Verizon.
23 percent of all of the breaches Verizon looked at were caused by actors identified as nation-state or state-affiliated, a figure that's up 12 percent from last year's report.
Extrapolating that data further, when it comes to attacks classified as cyberespionage, state-sponsored or nation-state attackers were responsible for 96 percent of breaches, with former employees, competitors, and organized criminals responsible for the remaining attacks.
When it comes to information breaches, the biggest cause of data disclosure was the misconfiguration of databases, oftentimes cloud storage services. According to Verizon, 36 percent of error-related breaches involved misconfigurations on databases.
These reports traditionally denounce the dangers of the insider threat and while insider misuse is still a concern, this year's report suggests that insiders aren’t being intentionally malicious as much as they’re being careless, leaking data by failing to configure servers or mistakenly publishing data to servers that shouldn't be viewable to the public.
When it came to breaking down miscellaneous errors that compromised security, Verizon found that 85 percent of them were caused by either misdelivery of sensitive data, publishing data to unintended audiences, or misconfigured servers.
This trend certainly isn't new, the unintentional actions of employees have long been an Achilles Heel for organizations but it sounds as if the incidents are really beginning to pile up however.
In addition to simply maintaining better security hygiene, Verizon's report encourages organizations to add integrity monitoring on payment sites, deploy two-factor authentication universally, and be vigilant when it comes to traffic spikes synonymous with DDoS attacks and cunning social attacks. The report also suggests tracking insider behavior by monitoring and logging access to sensitive data to ferret out employees who may not have the noblest of intentions.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.
