Most traditional security solutions tend to focus on infrastructure, but overlook the employee or contractor. This can create a blind spot, preventing you from knowing what data users are accessing and what they’re doing with it. This security void, combined with increasingly open networks among companies, contractors and suppliers, leaves your sensitive data vulnerable.
Digital Guardian delivers the broadest and deepest data visibility for information security professionals. Regardless of where the data resides, endpoints, shares, databases, or in the cloud, Digital Guardian can locate and track the movement of your sensitive data. Our agent provides complete visibility to all hardware, software, data creation, data storage and data movement. Our appliance analyzes databases, cloud storage and watches data in motion.
Related Resources
Solution Benefits
Continuously Records Every User Action with Sensitive Data
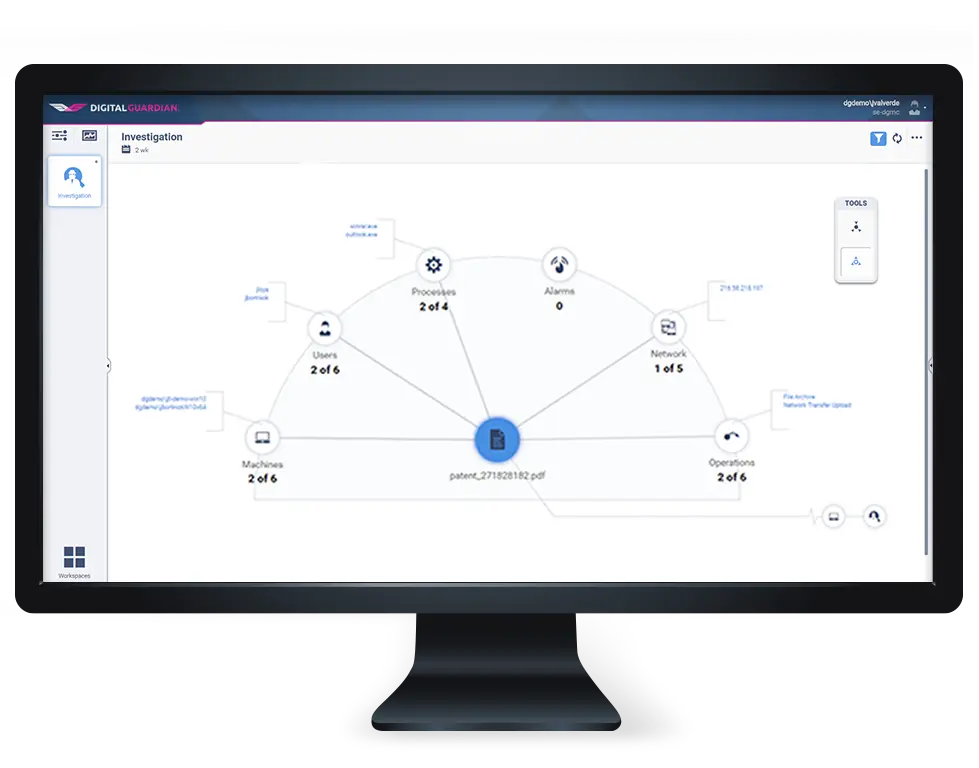
Track every system, data, application, and network event for each user. Detect abnormal file operations or unauthorized attempts to exfiltrate. Establish malicious intent by analyzing suspect actions in complete context. Capture files, screen shots and keystroke logging before and after suspicious activity.
Track every system, data, application, and network event for each user. Detect abnormal file operations or unauthorized attempts to exfiltrate. Establish malicious intent by analyzing suspect actions in complete context. Capture files, screen shots and keystroke logging before and after suspicious activity.
Identifies Suspicious User Behavior That Deviates from Normal Data Use
Establish user trends to baseline normal behavior and block/prompt/alert extreme exceptions. Identify suspicious or unauthorized applications used to access data. Detect suspicious system configuration changes. Alert when users deviate from normal activity.
Establish user trends to baseline normal behavior and block/prompt/alert extreme exceptions. Identify suspicious or unauthorized applications used to access data. Detect suspicious system configuration changes. Alert when users deviate from normal activity.
Monitors and Controls Privileged Users
Live and configurable reporting dashboards provide real-time insights into sensitive data location, usage and threats from insiders and outsiders.
Live and configurable reporting dashboards provide real-time insights into sensitive data location, usage and threats from insiders and outsiders.
Provides Chain of Custody Evidence to Prove Malicious Intent
Collect and preserve chain-of-custody forensic evidence including capture files, screenshots and keystrokes. Reconstruct incidents in their full context.
Collect and preserve chain-of-custody forensic evidence including capture files, screenshots and keystrokes. Reconstruct incidents in their full context.
We Can Prove It
Digital Guardian demonstrates an insider stole IP. The competitor was fined $100 million. Evidentiary-quality logs prove in court that the employee who was about to leave the company stole hundreds of pages of design information.
Schedule a Demo
See how Digital Guardian can help protect your critical data wherever it lives.