A group of European researchers and professors on Sunday disclosed a series of vulnerabilities in PGP and S/MIME, internet standards used for delivering end-to-end encrypted emails, that theoretically could be exploited to decrypt the plaintext contents of emails sent in the past.
There are no patches or even reliable fixes for the vulnerabilities; in lieu of a fix the researchers are encouraging users to disable the standards if they're using them for encrypted email.
The research, which is being referred to as “EFAIL,” was slated for publication on Tuesday but similar to January's Meltdown and Spectre vulnerabilities, the hype around the embargo was too much to sustain. This prompted researchers to publish the full details of their paper, “Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels," (.PDF) Monday morning.
We'll publish critical vulnerabilities in PGP/GPG and S/MIME email encryption on 2018-05-15 07:00 UTC. They might reveal the plaintext of encrypted emails, including encrypted emails sent in the past. #efail 1/4
— Sebastian Schinzel (@seecurity) May 14, 2018
Due to our embargo being broken, here are the full details of the #efail attacks. https://t.co/i7xAFwJ3WX
— Sebastian Schinzel (@seecurity) May 14, 2018
The underpinnings of the research stem from how email clients abuse active content, like externally loaded images or styles, in HTML emails. To exploit the flaws an attacker would first need to obtain encrypted email, either by eavesdropping on a network or by compromising an email account or server.
From there an attacker would have to change an email by adding embedded altered PGP or S/MIME cipher text and custom HTML and send it back to the victim. The recipient in turn would decrypt it, load external content, and trigger the exfiltration, one of two ways:
The first takes advantage of when the email software – Apple Mail, iOS Mail and Mozilla Thunderbird, etc. - displays the decrypted message as unencrypted. The client's HTML parser exfiltrates that message to a server the attacker controls.
The second is much more sophisticated and relies on using Cipher Block Chaining, or CBC, (in S/MIME) and Cipher Feedback Mode, or CFB (in in OpenPGP) gadgets to inject plaintext snippets into emails in order to exfiltrate data after decryption.
Blog Post What is Email Encryption? (Definition, Best Practices & More) |
As Matthew Green, a noted cryptographer and Assistant Professor of Computer Science at Johns Hopkins Information Security Institute, notes, the attack meets at the intersection of "bad crypto" and the "sloppiness" of mail client developers. In particular, he warns, the flaws could be exploited at a corporate email level, provided an attacker had access to stored emails.
The real news here is probably about S/MIME, which is actually used in corporate e-mail settings. Attacking and modifying encrypted email stored on servers could actually happen, so this is a big deal. 4/
— Matthew Green (@matthew_d_green) May 14, 2018
Werner Koch, the author of GNU Privacy Guard, a.k.a. GPG, dismissed the research as “overblown” on Monday.
“The topic of that paper is that HTML is used as a back channel to create an oracle for modified encrypted mails. It is long known that HTML mails and in particular external links like <img href="tla.org/TAG"/> are evil if the MUA actually honors them,” Koch wrote in an email to the Gnupg-users mailing list.
“There are two ways to mitigate this attack
- Don't use HTML mails. Or if you really need to read them use a proper MIME parser and disallow any access to external links.
- Use authenticated encryption,” Koch continued.
Robert J. Hansen, an Enigmail developer and GnuPG volunteer issued a statement on behalf of the standard Monday morning, urging caution in how the paper is interpreted.
“You might be vulnerable if you're running an ancient version of GnuPG (the 1.0 series; the current is 2.2), or if your email plugin doesn't handle GnuPG's warning correctly,” Hansen wrote, “You might also have had some exposure in the past if back then you used a pre-2000 version of GnuPG, and/or an email plugin which didn't handle the warning correctly.
1. This paper is misnamed. It's not an attack on OpenPGP. It's an attack on broken email clients that ignore GnuPG's warnings and do silly things after being warned.
2. This attack targets buggy email clients. Correct use of the MDC completely prevents this attack. GnuPG has had MDC support since the summer of 2000.
3. The authors made a list of buggy email clients. It's worth looking over their list of email clients (found at the very end) to see if yours is vulnerable. But be careful, because it may not be accurate -- for example, Mailpile says they're not vulnerable, but the paper indicates Mailpile has some susceptibility. The authors have done the community a good service by cataloguing buggy email email clients. We're grateful to them for that. We do wish, though, this thing had been handled with a little less hype. A whole lot of people got scared, and over very little,” Hansen tweeted.
There are arguments on both sides of the coin when it comes to the flaws. As Hansen/GnuPG notes a user would have to essentially blown past GnuPG's MDC warnings to be exploited. Some experts questioned Monday whether email clients should really treat MDC failures as warnings, instead of errors.
No, in 2018 you don’t get to claim the high ground and blame users and implementations if your crypto API returns the plaintext on a decryption error.
At most you can say “sorry we are a legacy system, no one knew better then, it’s time to migrate off”.— Filippo Valsorda (@FiloSottile) May 14, 2018
The idea that email clients should check for a “WARNING” message and abort is like the idea that they should supply special flags to curl to get it to check certificates.
No, gpg should do the right thing by default. It has one job!— Thomas H. Ptacek (@tqbf) May 14, 2018
MDC, or Modification Detection Code, is a cryptographic hash function introduced in 2000, designed to prove a message's integrity.
For what it's worth the authors of the paper, a group of academics from Münster University of Applied Sciences and Ruhr University Bochum in Germany, and KU Leuven in Belgium, called on PGP and S/MIME users to either disable encryption in their email clients or disable HTML rendering as a means to prevent active content abuse.
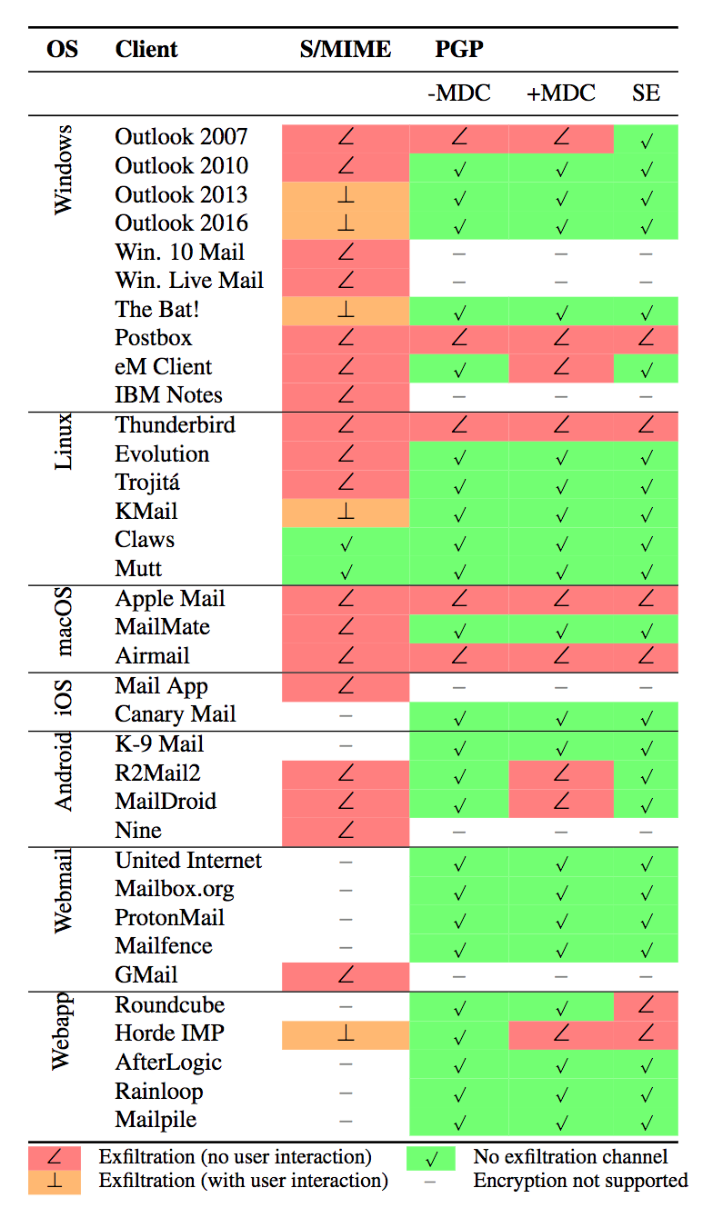
The second option, especially for the more security conscious, could be an especially fine option. As Claudio Guarnieri, a Senior Technologist at Amnesty International and Advisor at Citizen Lab notes, it could leave users less susceptible to phishing attacks.
Regardless of this particular issue, disabling HTML rendering in your email client is good. Less exposure to these sorts of attacks, fewer risks of getting remote resources accidentally loaded that might leak information, and easier to watch for potential phishing links.
— nex (@botherder) May 14, 2018
The Electronic Frontier Foundation (EFF) echoed the researchers' sentiments and encouraged users to immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email like Enigmail with Thunderbird, GPGTools with Apple Mail, and Gpg4win with Outlook.
ProtonMail, an end-to-end encrypted email service, took umbrage with the EFF's warning, calling it "overblown and disproportionate, and likely issued without fully understanding the issue," adding that the way the flaws were disclosed added insult to injury.
Efail is a prime example of irresponsible disclosure. There is no responsibility in hyping the story to @EFF and mainstream media and getting an irresponsible recommendation published (disable PGP), ignoring the fact that many (Enigmail, etc) are already patched.
— ProtonMail (@ProtonMail) May 14, 2018
ProtonMail, for its part, said Monday it was not affected by the flaws. The end-to-end encrypted email software Tutanota and Canary Mail, an email app with PGP for Mac and iPhone, also acknowledged their services weren't affected. Enigmail, as Hansen notes, patched the issues months ago.
"If you're using a recent GnuPG and Enigmail 2.0 or later, you should be fine. If you're not, consider this an object lesson in the importance of upgrading your security-critical software," he tweeted.
Keys image via Ozzy Delaney's Flickr photostream, Creative Commons

