Ransomware attacks are on a tear in 2016. Whether using updated versions of older ransomware families like CryptoWall or newer ransomware strains like Locky and TeslaCrypt, cybercriminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses. Recent cases of Locky infections impacting businesses include King’s Daughters’ Health hospital in Indiana and Methodist Hospital in Kentucky. The attack on Methodist Hospital was so crippling to its systems that IT staff had to declare an “Internal State of Emergency” while devices were restored one by one.
This demo uses a sample of the Locky ransomware deployed on a physical endpoint in a secure lab environment running Digital Guardian. This was actually a customer testing the DG Agent against Locky. Throughout this demo we’ll look at various DG alerts that would trigger the infection being blocked in a production environment, but for analysis, the ransomware was allowed to run through the entire infection sequence.
The infection sequence started with a double click on the sample; note this is not a typical entry vector we would normally see in the wild (e.g. email phishing or malvertising). Because of that, there are no entry vector attack alerts depicted here. Upon launch, we see some initial alerts that were generated by this execution. These alerts tell us that DG detected file extensions indicative of ransomware (common examples include .locky, .AESencrypted, .LOL, .OMG!) and that the ransomware sample was attempting to delete shadow copies of files to prevent victims from being able to recover their data once infected.
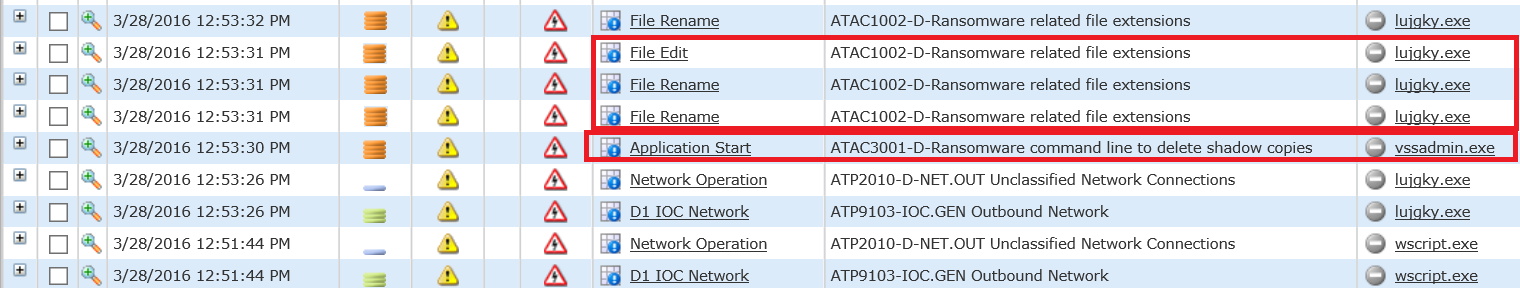
Looking further back into the event details of these alerts yields the dropped file, the IP address being used, and its malicious host domain. In this case, the dropped file is called 765f46vb.exe, the IP is 177[dot]185[dot]194[dot]115, and the malicious domain is comprecaldas[dot]com. It’s important to note that while this demo was conducted in a lab environment, this is a real sample of the Locky ransomware, and as such, this executable, IP address, and domain should be blocked.
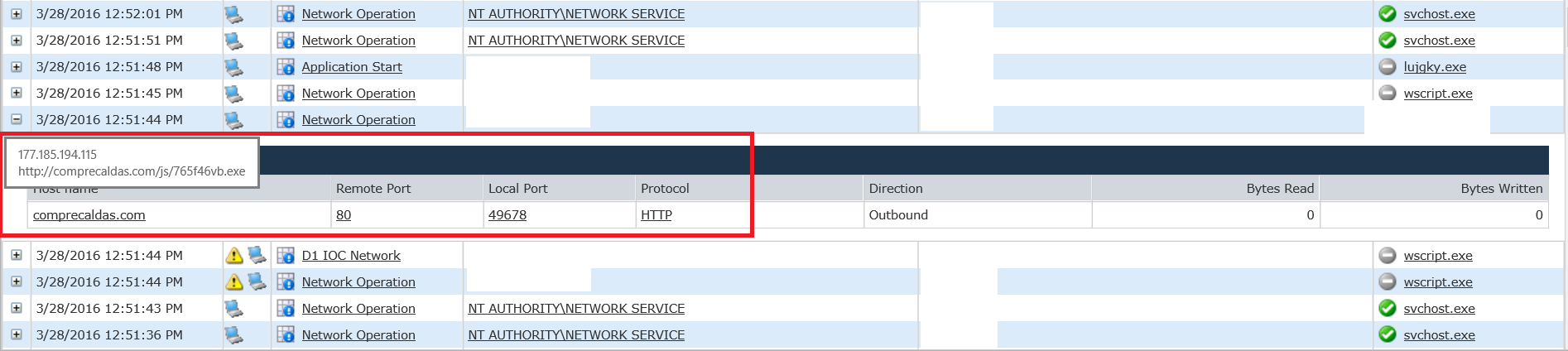
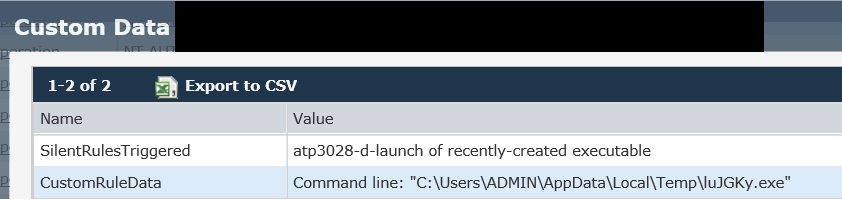
After double-clicking the sample, the native Windows scripting engine wscript.exe is seen making an HTTP callout to download the actual Locky variant. The executable launches a process called “lujgky.exe” (Locky), which triggers a silent alert for the launch of a recently-created executable.
Once Locky makes an outbound connection to the domain, it syncs its encryption key and executes its deletion of the shadow volume backups:

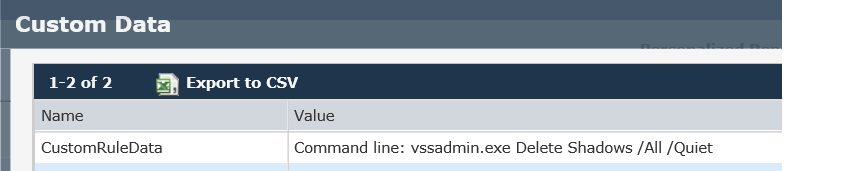
The above alerted-on command executes just prior to when Locky starts to encrypt documents on the machine, ensuring that the victim will have no native recovery method (shadow copies) and that their only chance at recovering their data would be restoring their last external backup, assuming a backup was done.
The encrypted files can be seen being renamed with .locky extensions:
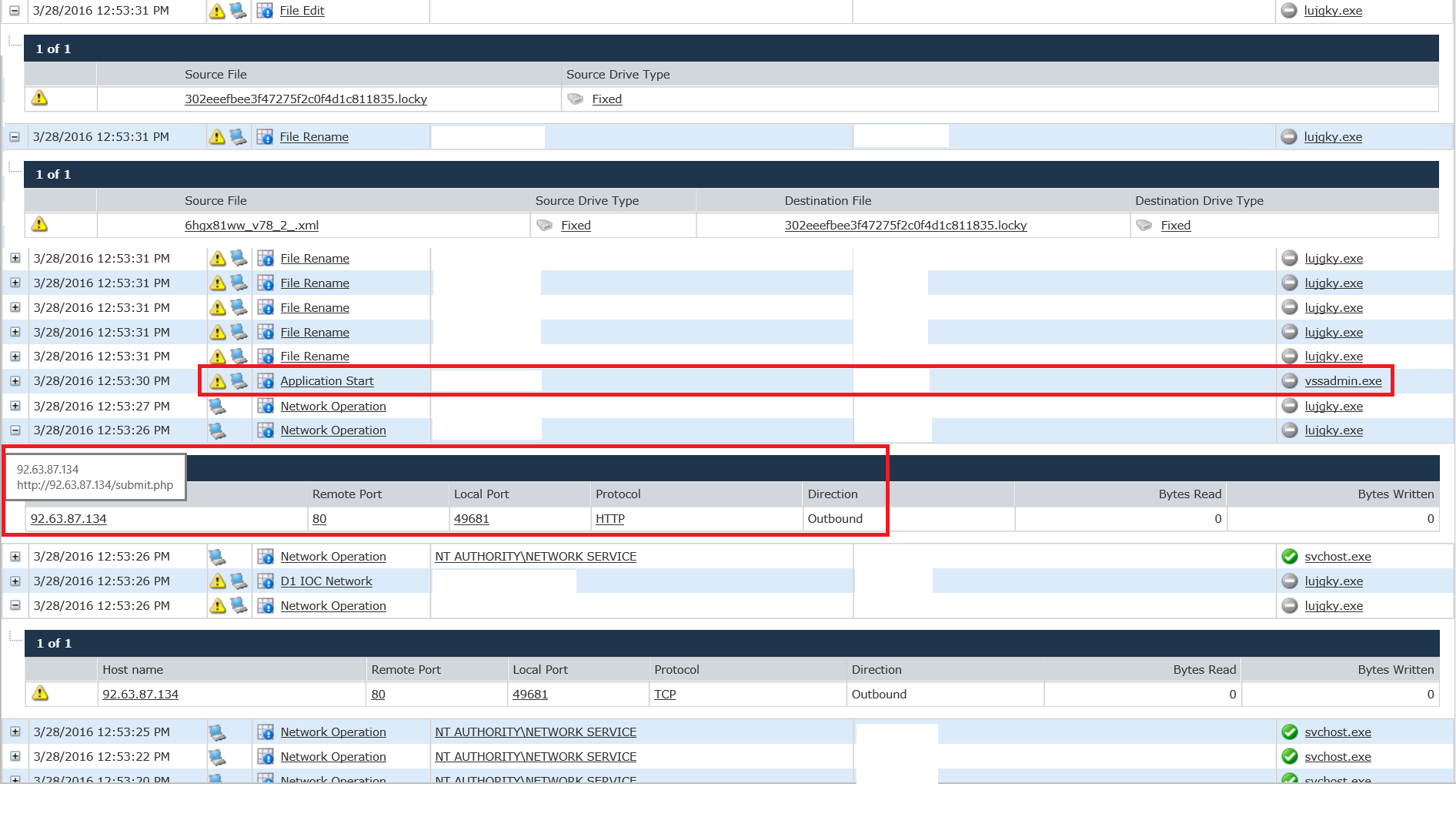
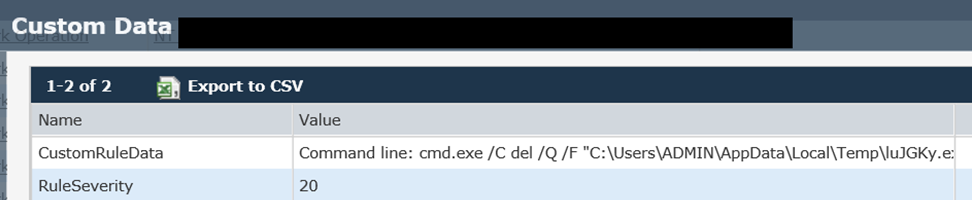
And finally, when the files have been encrypted, we see Locky deleting itself – the last stage of a successful attack:

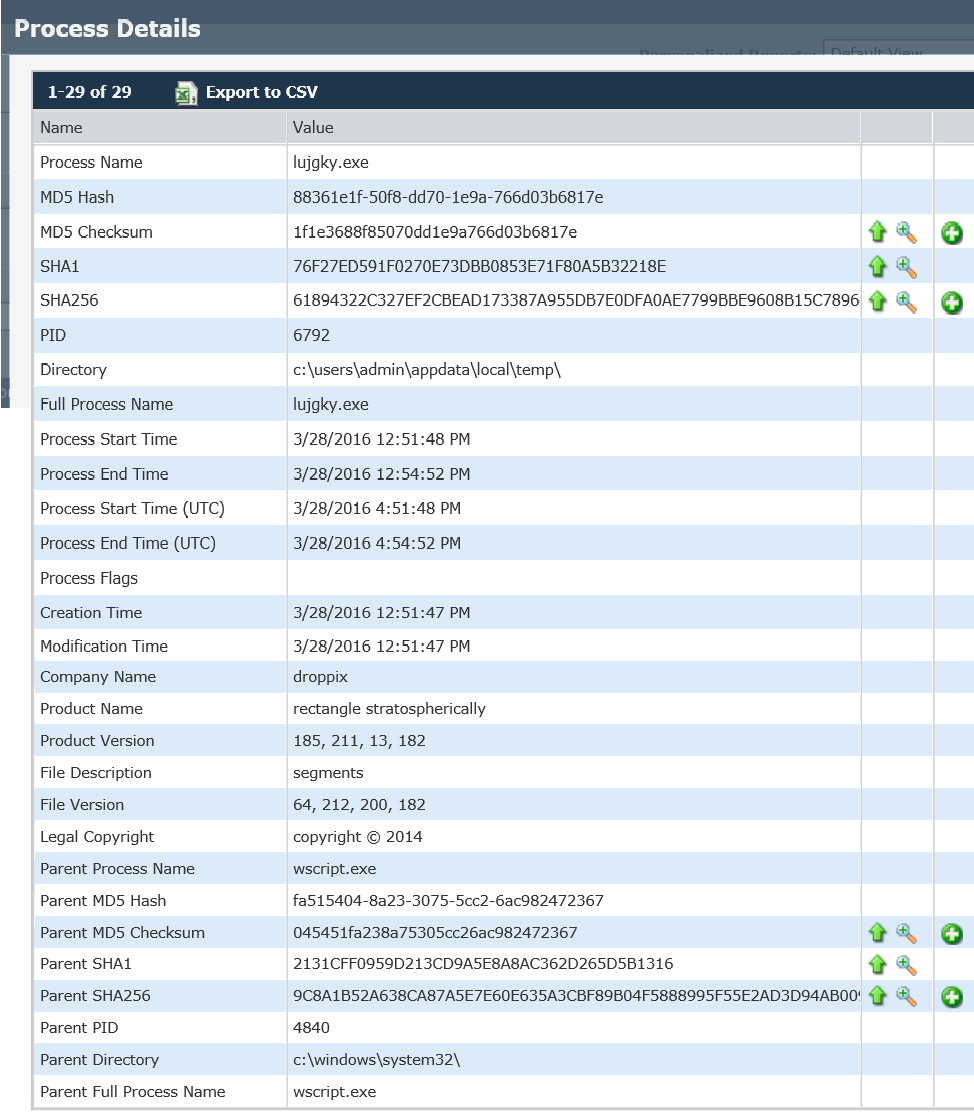
For investigative purposes, we’ve picked up additional details regarding this variant of Locky in our alerts process information screen. Note the executable name, MD5 checksum, and SHA256 – these should be blocked as well:
We just saw the typical infection sequence for a Locky ransomware variant. Having deep visibility into and correlation of file activity, network traffic, and new executable launches is critical to enable real-time detection and response to ransomware attacks. Beyond these capabilities, there are some basic security hygiene best practices that all organizations should follow to keep abreast of these threats.
Tips for Preventing Ransomware Infections
The following are some best practices that every business should implement to protect against ransomware attacks:
- User education: Often times users are the last line of defense and the most susceptible due to sentient choice. Educating users of possible attack methods and making sure they practice good online hygiene will go a long way in helping users avoid phishing and other social engineering attacks.
- Segregation: Users will fail, so where possible, separate workstations/machines that have access to sensitive data or critical systems from machines that have direct access to public internet services, such as email and general websites. Ransomware can’t encrypt sensitive files if it doesn’t have access to them on a machine that it infects.
- Application Whitelisting: For workstations/servers with dedicated functionality, install software that only allows explicitly defined programs to run and block all others. This works great for systems with single function legacy applications. Ransomware, even if executed, will not be able to run on these systems.
Looking to learn more about Fortra's Digital Guardian?
Have a question about data loss prevention, secure collaboration, or SaaS data protection? Don't hesitate to get in touch. We're here to help.
