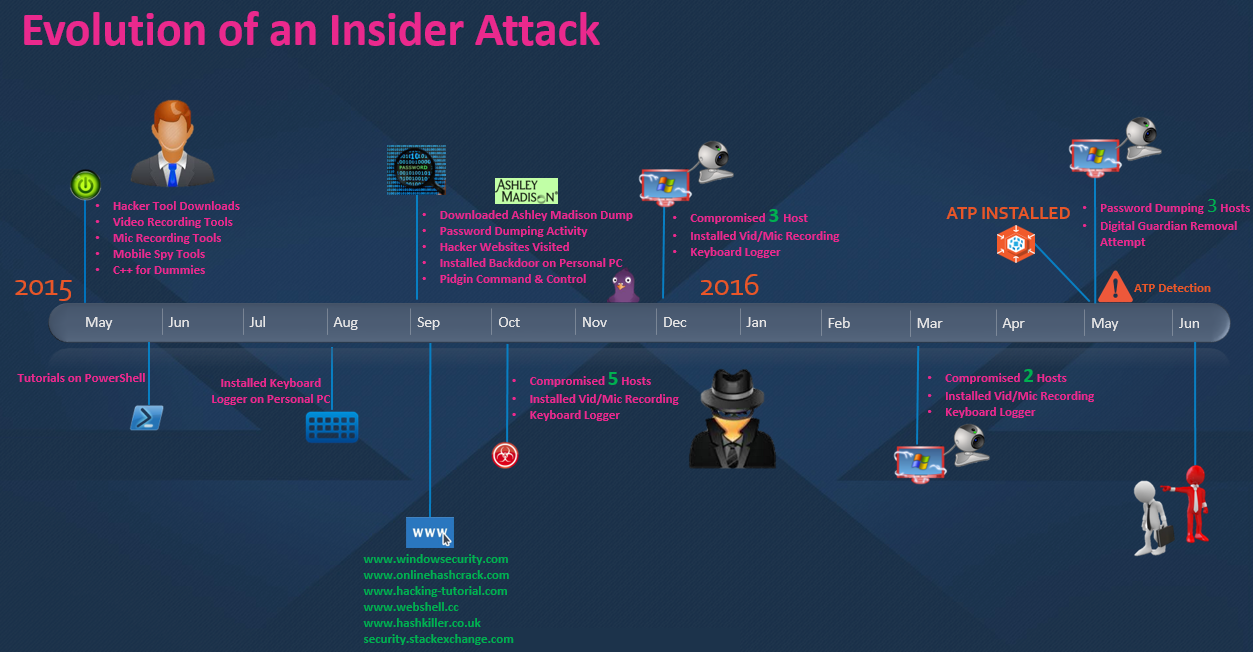
I call this tale "The Evolution of an Insider Threat: How a Business Analyst Turned into a Rogue Hacker." This activity was discovered immediately after deploying our Advanced Threat Protection (ATP) module to the environment. In order to tell this epic tale, we first had to acquire hard-drive forensics from the machine of interest, since this story commenced over a year ago. Let’s begin.
During the month of May 2015, a business analyst at one of our customer’s sites had downloaded a plethora of various hacker tools, video/mic recording software, and mobile spy tools to his desktop from a Chinese GitHub-type website. In total there were literally over a million individual files in this package containing both legitimate and nefarious applications. Some of the tools that were included in this package were items like WinVNC, Pidgin Chat Client, Filezilla FTP, Audacity, CamX, iSpy (mobile monitoring), etc. There were also a ton of source code files for the various tools. In addition to these tools, we also saw evidence of IT technical books and PDFs being downloaded such as “C++ For Dummies” and multiple tutorials on “How to Run Powershell.”

Images via For Dummies.
So on the surface, this is clearly somewhat odd. What would a business analyst be doing with all of this software, especially source code along with books on how to code in different programming languages? I’m not trying to stereotype here, but typically these types of analysts play in Excel spreadsheets all day crunching numbers. Not avidly reading about C++ and testing whether or not their “Hello World” program executes successfully.
But I digress…
Fast forward several months, and we begin to see a dramatic shift in this individual’s behavior from seemingly innocuous and inquisitive, to highly mischievous and malevolent. The activity starts out in September 2015 with the analyst visiting various hacker and cybersecurity websites like windowssecurity.com, hacking-tutorial.com, webshell.cc, and onlinehashcrack.com. Then why not add in for good measure a download of the entire Ashley Madison dump containing names, street addresses, emails, phone numbers, and credit card transactions from nearly 33 million accounts? This literally keeps getting better. Next we see this business analyst testing out some of his recently acquired Powershell coding skills via the execution of password dumping programs written in the language. And finally he installs a highly customized backdoor on his work laptop that leverages the instant messaging chat client Pidgin for issuing command and control and the FTP protocol to exfiltrate encrypted data out to a website he manages via a web hosting provider. I must say, that escalated rather quickly!
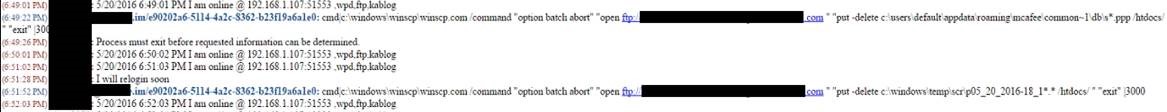
Command and Control Log
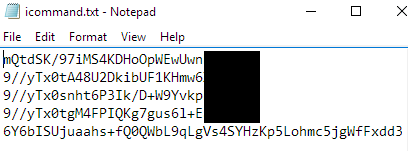
Encrypted Files
So let’s recap. Business analyst downloads a ton of tools and books. Ups his knowledge and develops a highly customized backdoor while taking an interest in one of 2015's highest profile website compromises. This almost sounds like an episode out of Mr. Robot - or I’m just overly anxious about Season 2 airing next week! Moving forward into the month of Halloween, which is quite fitting for the scenario, this ghoul on the network now begins to target his fellow employees. He installed his uber awesome, slightly noobish backdoor and keylogger on 5 different machines and then several more around the Christmas holiday. I’m willing to bet those employees would’ve declined that gift, had they been aware that 1) it was even given to them and 2) it was capturing video through their laptop camera, recording their daily discussions, and logging all of their strokes on the keyboard. And let’s not forget to mention, one of his targets was his own wife’s work laptop. Yes, surprisingly we found out his wife works at this company as well. Why not test out his malicious invention on her machine too? I'm willing to bet she had no clue either, but that’s just an assumption, of course, with minimal farfetchedness. And yes, that’s a word I Googled to ensure it was a real one!

Image via Mr. Robot/USA Network.
At this point in the game, the employee charges ranged from wasting company time to increasing risk to the network by installing unauthorized software on his work laptop, downloading morally questionable material, violating the privacy of other employees, hacking into corporate resources, and quite frankly just being kind of creepy. There’s some more context to that creeper comment since we uncovered what appeared to be surveillance-type photos taken of another female employee coming in and out of the building they both worked in. #NotCool.
For the next two months, Mr. Blackhat (a term used to commonly describe malicious hackers), laid low a bit. He was focusing on his current investments and stock selections to ensure for an adequate return in the new year. Once that was ironed out, it was back to his playland in March 2016 where he began installing his backdoor on even more devices! Then the month of May rolls around. A month that was very significant for this company since we commenced rolling out our Advanced Threat Protection module to their environment. Not even a day into the rollout, the ATAC team picked up on this activity, even seeing attempts by him to remove our Digital Guardian Agent, and we immediately alerted the organization. As we began to unravel what we were seeing in the logs on the first day, we identified at least 10 machines with some type of indicator linked to this individual’s activity. I knew this was going to require ‘Boots-on-Ground’ incident response to lend a hand with all the forensics; so I booked my flight and arrived the next day.

At this point, we knew very little in the grand scheme of things. We had no idea how the threat even got in since ATP wasn’t installed prior, but we immediately began pulling forensics off of all the involved machines. I deployed my infamous ‘Forensicator’ tool to grab specific files of interest like $MFT, Event Logs, Registry, etc. and started parsing through the files with a tool called log2timeline to build exactly what the name implies: a timeline of all the logs. Now we were left with millions and millions of log entries that we needed to whittle down to the juicy stuff. Conducting that process ultimately led to the details I’ve discussed above about how this entire story played out from the beginning. In addition to that, we discovered in total 25 machines that were affected by his escapades. Armed with this information, our customer hopped a flight to this individual’s location for a quaint chat. I would’ve paid to see the look on his face when what all we found was disclosed to him, but apparently the meeting was completely anti-climactic. What do I mean? He actually played dumb.
OK, this is where things can get a bit tricky sometimes. An employee can very easily say "I have no idea what you’re talking about," or "It wasn’t me, I’ve been hacked!" But at the end of the day, forensics don’t lie, which is why I always highly recommend having this capability either in-house or on call from a third party who knows what they’re doing. All of the files he downloaded and used were stored in a folder called “Personal”; not some obscure temporary directory where a true hacker would most likely leave behind their toolset. His command and control FTP infrastructure was registered in his name. Sure he could’ve been framed, but really? His logon/logoff times corresponded to the nefarious actions he was taking while working. He’d SUM up some cells in Excel, then when he got bored he switched over to controlling his backdoors. I could probably go on forever here, including his web browsing habits to hacker sites and files of interest even residing on his desktop in plain view for him to see, but ultimately I didn’t have to. A day after the meeting, this individual broke down to his manager and confessed to everything. He was immediately let go from the company and I’m sure they're now investigating a bit further into his wife’s activity and knowledge of the incident as well. The company has continued to expand their security program with Digital Guardian and remains prepared to tackle all insider and outsider threats.

Throughout all this this, there were a ton of twists and turns in the case over the course of the several days that we focused on it and it literally almost felt like something out of Dan Brown’s Da Vinci Code. Granted the story line is completely different, but the exhilarating feeling of finding one clue after the next and decrypting encoded artifacts is why I truly love this job. There’s never a dull day at ATAC and we’re always looking for superior talent to ensure our customer’s most sensitive assets are protected! So chalk one up for the ATAC team and now on to the next case.
Looking to learn more about Fortra's Digital Guardian?
Have a question about data loss prevention, secure collaboration, or SaaS data protection? Don't hesitate to get in touch. We're here to help.
