
TechTarget defines a data breach as “an incident in which sensitive, protected, or confidential data has potentially been viewed, stolen, or used by an individual unauthorized to do so. Data breaches may involve payment card information (PCI), personal health information (PHI), personally identifiable information (PII), trade secrets, or intellectual property.” But how long have data breaches been a concern for companies and consumers, and what kind of impact have data breaches had throughout history?
The Origin of Data Breaches
Data breaches have gained widespread attention as businesses of all sizes become increasingly reliant on digital data, cloud computing, and workforce mobility. With sensitive business data stored on local machines, on enterprise databases, and on cloud servers, breaching a company’s data has become as simple – or as complex – as gaining access to restricted networks.
Data breaches didn’t begin when companies began storing their protected data digitally. In fact, data breaches have existed for as long as individuals and companies have maintained records and stored private information. Before computing became commonplace, a data breach could be something as simple as viewing an individual’s medical file without authorization or finding sensitive documents that weren’t properly disposed of. Still, publicly-disclosed data breaches increased in frequency in the 1980s, and in the 1990s and early 2000s, public awareness of the potential for data breaches began to rise.
Laws and regulations such as HIPAA or the PCI Data Security Standard are created to provide guidelines for companies and organizations handling certain types of sensitive consumer information. These regulations provide a framework for the required safeguards, storage, and use practices for handling sensitive information, but these rules don’t exist in all industries, nor do they definitively stop data breaches from occurring.
Most information on data breaches focuses on the time period from 2005 to today. This is largely due to the advancement of technology and proliferation of electronic data throughout the world, making data breaches a top concern for both enterprises and consumers. Today’s data breaches can impact hundreds of thousands – often millions – of individual consumers, and even more individual records, all from a single attack on one company.
4 Common Types of Data Breaches
When large organizations “lose” or accidentally expose data, it’s often through hacking, negligence, or both. However, there are several other types of data loss and/or corruption that would be classified as a “breach.” Let’s take a look at four additional types of breaches.
Ransomware
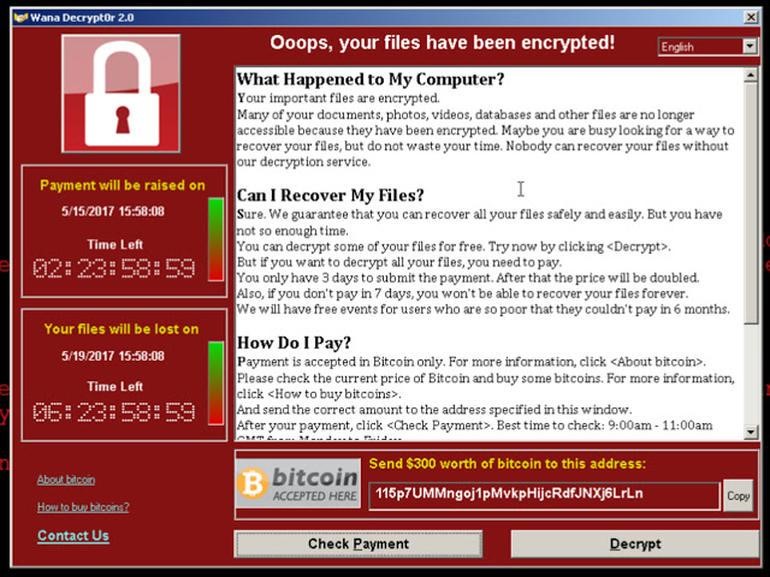
Image via ZDNet.
Ransomware is the name for malicious software which gains access and locks down access to vital data (i.e., files, systems). These attacks most commonly target businesses. Files and/or systems are locked down and a certain fee is demanded (most often in the form of Bitcoin or other cryptocurrencies).
Malware
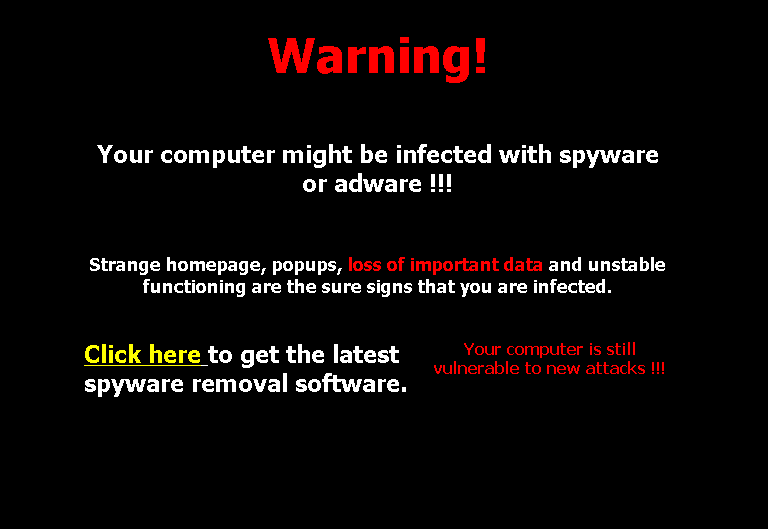
Image via OnlineCMag.
Malware is any software designed to harm computer files and/or systems. Ironically, malware often masquerades as a warning against malicious software in an attempt to convince users to download the very types of software mentioned in the “warning” message.
Phishing
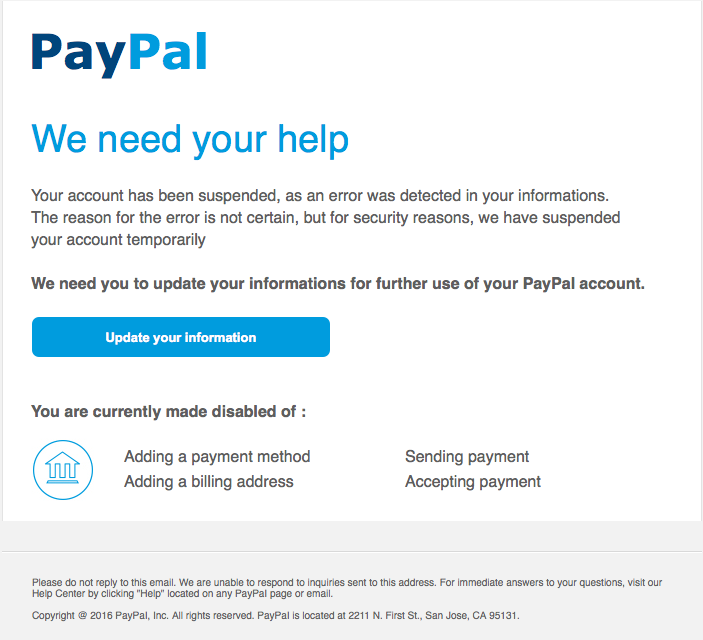
Image via EDTS.
Phishing occurs when someone or something mimics a trusted, reputable entity in order to collect sensitive data (often banking or highly personal details). These attacks are not exclusive to the Internet. Common methods for phishing scams can include:
- A pop-up on your browser
- An email with a link
- A person on the phone claiming to be a representative of a reputable company
Denial-of-Service (DoS)
Image via GregThatcher.com.
A denial-of-service (DoS) breach essentially takes away access to websites and webpages. When this happens at large scale, it’s known as a distributed denial-of-service (DDoS). These large-scale attacks can disrupt a large portion of sites online in certain areas. One of the largest DDoS attacks on record is the 2016 attack on Dyn which made a considerable portion of Eastern U.S. Internet access virtually unusable for several hours. The largest and most recent DDoS attack happened to GitHub in February of 2018.
How Many Data Breaches Occur?
The Privacy Rights Clearinghouse, which reports on data breaches impacting consumers, maintains a chronology of data breaches and security breaches dating back to 2005. The data breaches reported by the Privacy Rights Clearinghouse include breaches in which the information compromised “includes data elements useful to identity thieves, such as Social Security numbers, account numbers, and driver's license numbers.”
However, some breaches that do not compromise this type of sensitive information are also reported in order to provide a broad view of the variety and frequency of data breaches. Additionally, the data breaches reported here include only those reported in the United States, not incidents in other countries.
Most Historical Accounts Document Breaches from 2005 Onward
While data breaches were certainly occurring prior to 2005, most of the biggest data breaches recorded in history are reported in 2005 or beyond. This can be attributed to the fact that the world’s volume of data has been growing exponentially year after year, giving cyber criminals a greater opportunity to expose massive volumes of data in a single breach.
Image via CSC.com.
Consider these projections from a 2012 report by CSC:
- By 2020, over one-third of all data will live in or pass through the cloud.
- In 2020, data production is estimated to be 44 times greater than it was in 2009; experts estimate a 4,300 percent increase in annual data generation by 2020.
- While individuals are responsible for most data creation (70 percent), 80 percent of all data is stored by enterprises.
In 2005 alone, 136 data breaches were reported by the Privacy Rights Clearinghouse. More than 4,500 data breaches have been made public since 2005, with more than 816 million individual records breached. Because the Privacy Rights Clearinghouse reports on breaches for which the number of records breached is unknown and is not a comprehensive compilation of all breach data, the actual total records breached as a result of data breaches is likely substantially higher. For instance, the 2015 Verizon Data Breach Investigations Report covered over 2,100 data breaches in which more than 700 million records were exposed for the year 2014 alone.
Data Breaches Have Become Larger in Number and Impact
Several experts and other media outlets have attempted to name the largest data breaches in history. According to Statista, which reports on the number of data breaches and records exposed in the United States since 2005, the number of cyber attacks is on an upward trend. In 2005, 157 data breaches were reported in the U.S., with 66.9 million records exposed. In 2014, 783 data breaches were reported, with at least 85.61 million total records exposed, representing an increase of nearly 500 percent from 2005. That number more than doubled in three years to 1,579 reported breaches in 2017. And those are Statista’s numbers, which are somewhat conservative when compared to the Verizon DBIR or other industry-standard data breach reports.
Image via Statista.com.
The trend is not increasing consistently, however. In 2009, for example, the number of total data breaches reported in the U.S. dropped to 498, from 656 in 2008. That said, the total number of individual records exposed increased sharply, from 35.7 million in 2008 to 222.5 million in 2009. These figures indicate that while fewer breaches occurred, the individual breaches were larger, resulting in a greater number of records exposed per breach.
There was also a decline in the number of data breaches reported between 2010 and 2011, with 662 data breaches reported in 2010, and 419 data breaches reported in 2011. Since 2011, however, the number of data breaches reported in the United States has been rising steadily:
- 614 data breaches reported in 2013
- 783 data breaches reported in 2014
- 1,093 data breaches reported in 2016
- 1,579 data breaches reported in 2017
Forbes reports that over the past 10 years, there have been more than 300 data breaches resulting in the theft of 100,000 or more records. And those are only some of the data breaches that were publicly reported.
The Largest Data Breach in History
The largest data breach in history indirectly involved Experian, one of the three main credit reporting agencies. Experian acquired a company called Court Ventures, which gathers and aggregates information from public records, in March 2012. At the time of acquisition, Court Ventures had a contract with a company called U.S. Info Search. The contract enabled customers of U.S. Info Search to access the company’s data to find individuals’ addresses that would help them determine which court records to review.
Court Ventures sold information to a number of third parties, including a “Vietnamese fraudster service,” which then provided its own customers with the opportunity to look up personal information of Americans, including financial information and Social Security numbers, which was then used for identity theft in many cases.
As Experian explains, “After Experian’s acquisition of Court Ventures, the U.S. Secret Service notified us that Court Ventures had been and was continuing to resell data from a U.S. Info Search database to a third party, possibly engaged in illegal activity. The suspect in this case posed as a legitimate business owner and obtained access to U.S. Info Search data through Court Ventures prior to the time Experian acquired the company.” Experian maintains that no Experian databases were breached; U.S. Info Search’s databases were the source of the consumer information.
Some news sources cite 200 million records breached in this incident, which continued for more than 10 months after Experian acquired Court Ventures, although DataBreaches.net reports that 200 million is the figure representing the total number of records stored in the database that was breached. The actual number of records exposed, according to Experian, is unknown, but believed to be much lower.
Other Major Data Breach Examples
While the Experian/Court Ventures incident is often cited as the largest data breach in history, there are certainly many other data breaches that have gained widespread recognition as having substantial impact, or at minimum, threat of potentially significant impact, on consumers.
In 2008 and 2009, Heartland Payment Systems suffered a data breach resulting in the compromise of 130 million records. A New Jersey-based payment processor, Heartland Payment Systems’ data was breached through malware that was planted on Heartland’s network, recording credit card data as it arrived from retailers, Tom’s Guide reports. This data, obtained through Heartland’s payment processing services for more than 250,000 businesses, was then exposed to cybercriminals. This data breach is regarded as the largest credit card scam in history.
Slate.com visualizes the largest data breaches in history since 2005 in an infographic that illustrates whether breaches were the result of hacks, accidental publication, inside jobs, lost or stolen computers, lost or stolen media, poor security, viruses, or unknown causes.
Image via Slate.com.
The majority of the largest breaches recorded resulted from hacking attacks, while one of the earliest reported data breaches, impacting AOL and compromising 92 million records in 2005, was reported as an inside job. Another AOL breach in 2006 resulted from accidental publishing of sensitive data; this breach compromised 20 million records.
A data breach impacting the U.S. military is another notable exception to the rule, with 76 million records compromised in 2009 as the result of lost or stolen media. Other notable major data breaches not previously discussed include:
- TK/TJ Maxx: 94 million records compromised in 2007
- Sony PlayStation Network: 77 million records compromised in 2010
- Sony Online Entertainment: 24.6 million records compromised in 2011
- Evernote: 50 million records compromised in 2013
- Living Social: 50 million records compromised in 2013
- Target: 70 million records compromised in 2013
- Ebay: 145 million records compromised in 2014
- Home Depot: 56 million records compromised in 2014
- JP Morgan Chase: 76 million records compromised in 2014
- Anthem: 80 million records compromised in 2015
- Yahoo: One billion records compromised in 2016
- Deep Root Analytics: 198 million voter records in 2017
This data, particularly in light of the fact that most of these breaches are carried out by hackers, indicates that data breaches are becoming more widespread – and having a much larger impact, compromising millions of records containing sensitive consumer, company, or user data.
With even the world’s largest companies suffering massive data breaches, modern enterprises require a comprehensive, full-circle approach to data protection and security. The reactive approaches of yesterday simply won’t cut it in the modern threat landscape. If you want to learn more about the data breaches, read our list of the top 10 manufacturing data breaches in the 21st century.
Data Breach Insurance
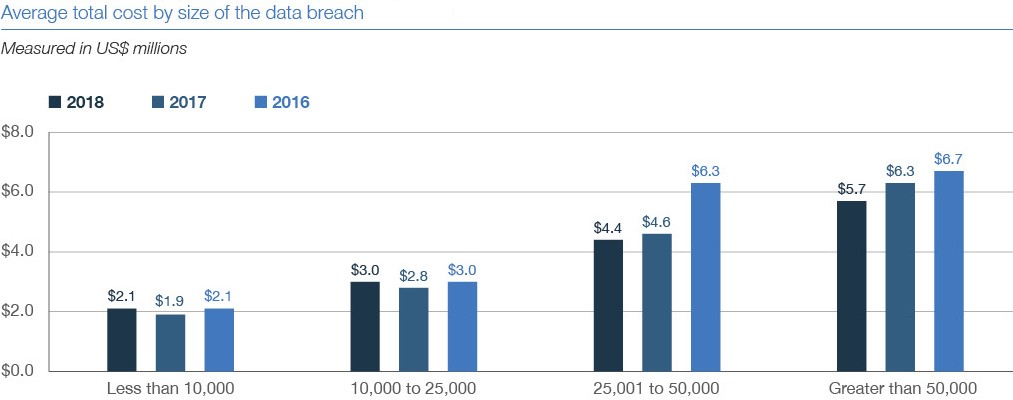
According to 2018 research, the average cost per record lost in a data breach is $148. The average total costs of a breach is $3.86 million. Even a small business with 1,000 lost records could see costs in the tens of thousands.
In order to mitigate the risk that comes along with data loss, many companies are now purchasing data breach insurance.
Screenshot via SecurityIntelligence.
Types of Data Breach Insurance
First-Party Insurance
There are many different consequences that occur as a result of a data breach — each with their own cost. From sending notifications to recovering data, time and money will be spent in amounts that could crush any business.
First-party insurance covers these expenses, including:
- Notifying all affected parties
- Costs of investigating details of the breach
- Fielding inquiries from all affected parties
- Tools to help affected parties (e.g., credit reporting)
Third-Party Insurance
Primarily used by contractors and IT professionals, third-party insurance covers those who work with companies who could be hacked. Companies and professionals hired to perform technical tasks (install hardware, software, etc.) can be subject to lawsuits in the event that the hiring party has a data breach. The covered expenses may include things such as lawyer/court costs and settlements.
Data Breach Defense and Prevention Resources
With the ever-increasing number of security threats to enterprises, small businesses, and personal security, data breach defense and prevention has advanced accordingly. Modern solutions offering great protection and a more proactive approach to security to ensure the safety of sensitive information. The following resources offer additional information on the advancement of data protection and valuable tips for preventing data breaches.
Members of the U.S. House of Representatives House Energy and Commerce Committee have advanced a bill that addresses the increased threat of cyber crime to consumers. “The Data Security and Breach Notification Act is a bipartisan solution to address the growing problem of cyber crimes and protect vulnerable information from criminals. The legislation establishes a nationwide safety regime for data protection and breach notification.”
Verizon’s annual Data Breach Investigations Report has become a security industry favorite for its assessments of thousands of data breaches that it investigates with the help of the U.S. Secret Service and several partnering security organizations. Every year the DBIR sets out to analyze major trends in data breaches, victims being targeted, attack patterns, and more.
IT Business Edge provides a slideshow illustrating 8 Ways to Prevent Data Breaches, including tips such as instituting end user security awareness, performing regular vulnerability assessments, and other helpful tactics.
Data Breach Today is a multimedia news resource and a robust source of information on the latest data breaches, their impact, and strategies for preventing companies from falling victim to cyber criminals.
Data Breach Watch is another resource reporting on discovered data breaches, news, and trends impacting both consumers and companies in every vertical.
The Global Privacy & Security Compliance Law Blog is an excellent resource for companies faced with stringent and ever-changing security regulations and compliance requirements.
The Hill takes a critical look at data breach prevention practices in light of the alarming statistics on the number of data breaches and their subsequent fallouts in 2014. As this article points out, the number of data breaches that involved 100 million customer records or more doubled in 2014. In fact, one billion data records were either lost or stolen in 2014, a 71 percent increase over 2013. “It’s time that executives and information security professionals accept the fact that their companies will be breached and start thinking outside the box when it comes to data security. To be in denial of this truth is to not accept reality.”
This article from The New York Times discusses strategies for minimizing the risk of a data breach in light of the major breaches impacting some of the world’s largest companies in recent history. One suggestion, for instance, is minimizing or eliminating the unnecessary storage of data. “Companies also need to think carefully about what data they are collecting and storing. By keeping lots of sensitive information, they place themselves and their customers at considerable – and in some cases unnecessarily greater – risk than if they had deleted the data or never collected it. To take one startling example, security experts say there was absolutely no reason for Target to have stored the four-digit personal identification numbers, or PINs, of their customers’ debit cards.”
Tom’s IT Pro reports on new tools and technologies for preventing data breaches following the 2014 SecureWorld Expo.
While no company wants to suffer a data breach, healthcare providers and their business associates stand to lose even more from a data breach, with penalties under HIPAA for inadequately protecting personal health information. CIO takes a look at the risks of a data breach in the healthcare industry, offering 12 tips to prevent a healthcare data breach.
According to this article from TechTarget, “Assumption of breach is the new norm.” The article goes on to describe how this critical shift in thinking is being used to create more stringent, comprehensive data breach protection policies and protocols.
As many of these sources point out, 2014 was a record-breaking year for data breaches, renewing the focus on the need for better methods for both preventing and responding to the (inevitable) data breach. This 60-minute webinar training from Bank Info Security discusses “The Changing Landscape of Data Breaches & Consumer Protection in 2015.” The full webinar will be available on-demand soon.
Experian itself was subjected to the perils of the aftermath of a data breach, and it has released its fifth annual Data Breach Industry Forecast for 2018. The report provides an overview of data breach trends and the outlook for 2018 while emphasizing the need for companies to have a data breach response plan.
Holland & Knight takes a look at “How Recent Data Breaches are Changing the Face of Cybersecurity for the Private Sector.”
We at Digital Guardian regularly cover the topic of data breaches and provide insights on both preventing and responding to a data breach. In this expert roundup, we ask 30 data security experts to share the most important next step you should take following a data breach. In another roundup, we asked 27 data security experts for their insights on the most cost-effective ways startups can protect themselves from data breaches. To help your employees with cyber awareness, we also created a Cybersecurity Awareness Kit. Be sure to follow our blog for updates on the latest data security information, research, and discussions, and visit our resources section for analyst reports, case studies, data sheets, and other resources on data breach prevention and data security.
Looking to learn more about Fortra's Digital Guardian?
Have a question about data loss prevention, secure collaboration, or SaaS data protection? Don't hesitate to get in touch. We're here to help.




