Digital Guardian’s approach to cyber threat detection takes two primary angles which include Real-Time Detection (RTD) and Historical Detection (HD). I’ll break down both areas into the fundamental capabilities that currently exist today within the product to provide an overview of what the product can deliver for host-based detection.
Real-Time Detection:
RTD is arguably the most critical type when referring to incident discovery across your enterprise. At any point in the day or at night, a compromise can occur in a matter of seconds, leaving your organization’s most sensitive assets at risk. The DG agent continuously collects Data Events, User Events, and System Events as they occur on the machine and stream this data up to a centralized console. See below for examples of these event types:
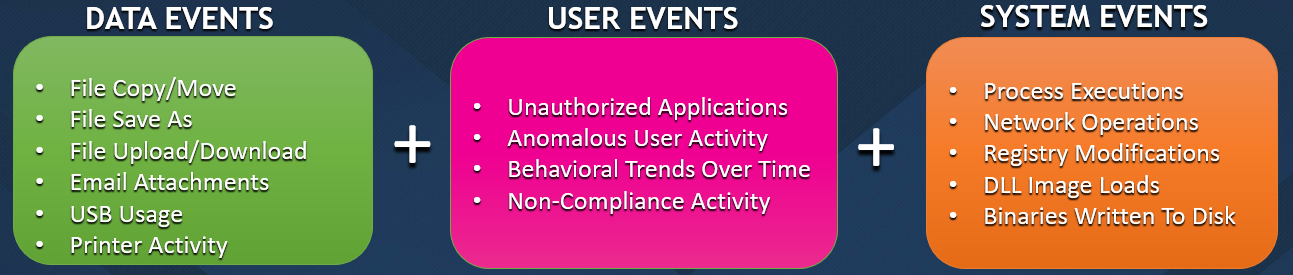
Each of the event types above also provide a wealth of metadata associated with it, to provide forensic analysts a mountain of possible indicators. For example, under the System Events section the agent will collect every process execution that occurs. Each execution also includes information like:
• Application Name
• File Path
• MD5/SHA1/SHA256
• Company Name
• Product Version
• Filesystem Timestamps
• VirusTotal Data
• Parent Information
• Command Line
• Signature Status
• Signature Issuer & Publisher
• Number of Files Modified
• Number of Network Connection
• Number of Registry Keys Modified
There are currently over 80 metadata fields being acquired so this is just a small subset. With this information, we can now leverage the agent’s internal signature engine to develop high fidelity threat rules. These threat rules can be single threaded in nature, whereby we look for specific command line strings or names of output files that are commonly generated by password dumping programs, or we can use a correlation framework which provides greater context to various activities. For example, let’s say Adobe Acrobat Reader writes an executable file, Reader then executes a command which then causes the executable to make an outbound connection to the internet. This sequence of events can be a compounded correlated rule with a higher weighted risk which warrants further investigation.
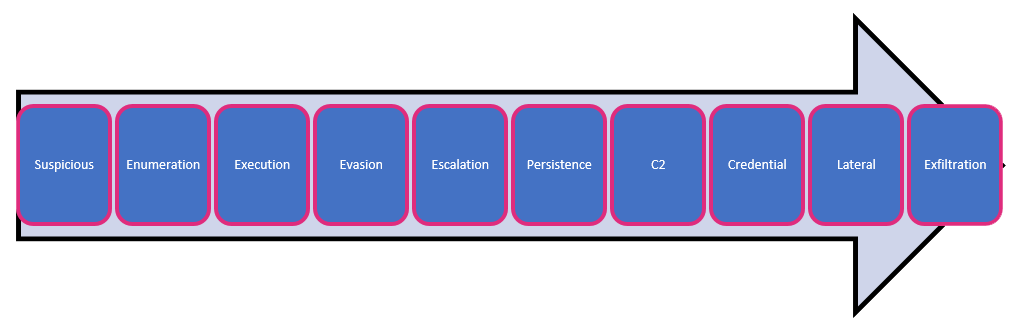
Today there are close to 200+ behavioral based rules that are included with the ATP policy pack.
These rules cover the entire attack lifecycle ranging from initial infiltration type activity, to execution, command and control, right through lateral movement and exfiltration. Having a layered approach to RTD is critical in case one phase is potentially missed.
On Monday we'll cover Digital Guardian's Historical Detection capabilities.
