An Italian IT company is believed to be behind a powerful new strain of Android spyware capable of surveilling WhatsApp messages, recording audio, and being able to silently connect to malicious Wi-Fi networks.
Researchers at Kaspersky Lab, who discovered the malware and disclosed their findings on Tuesday, named the threat Skygofree after coming across the word in one of the attackers’ domains.
While the malware wasn’t identified until October 2017, researchers suggest that some of Skygofree’s domains date back to 2015. Some early samples and signatures of the malware suggest it may even date back to 2014. The latest iteration of Skygofree the researchers analyzed is signed with a certificate from September 14, 2017, and the latest domain connected to the malware was registered on October 31, 2017 - two signs that whoever’s behind the spyware has continues to upgrade it throughout the years.
Skygofree has all of the requisite traits of a spyware implant: It can sniff exfiltrated data like call records, text messages, geolocation data, external audio, calendar events, and other memory information.
After it receives a special command it downloads a specialized payload to steal information from external apps. One payload takes aim at WhatsApp and via Accessibility Services, a feature designed to assist users with disabilities in using Android devices, to steal text messages.
“The payload uses the Android Accessibility Service to get information directly from the displayed elements on the screen, so it waits for the targeted application to be launched and then parses all nodes to find text messages,” Nikita Buchka and Alexey Firsh, mobile security researchers with the firm, wrote Tuesday. “Note that the implant needs special permission to use the Accessibility Service API, but there is a command that performs a request with a phishing text displayed to the user to obtain such permission.”
According to researchers the malware was being distributed through fake but legitimate looking network provider update pages, including ones designed to mimic the telecoms Three and Vodafone.
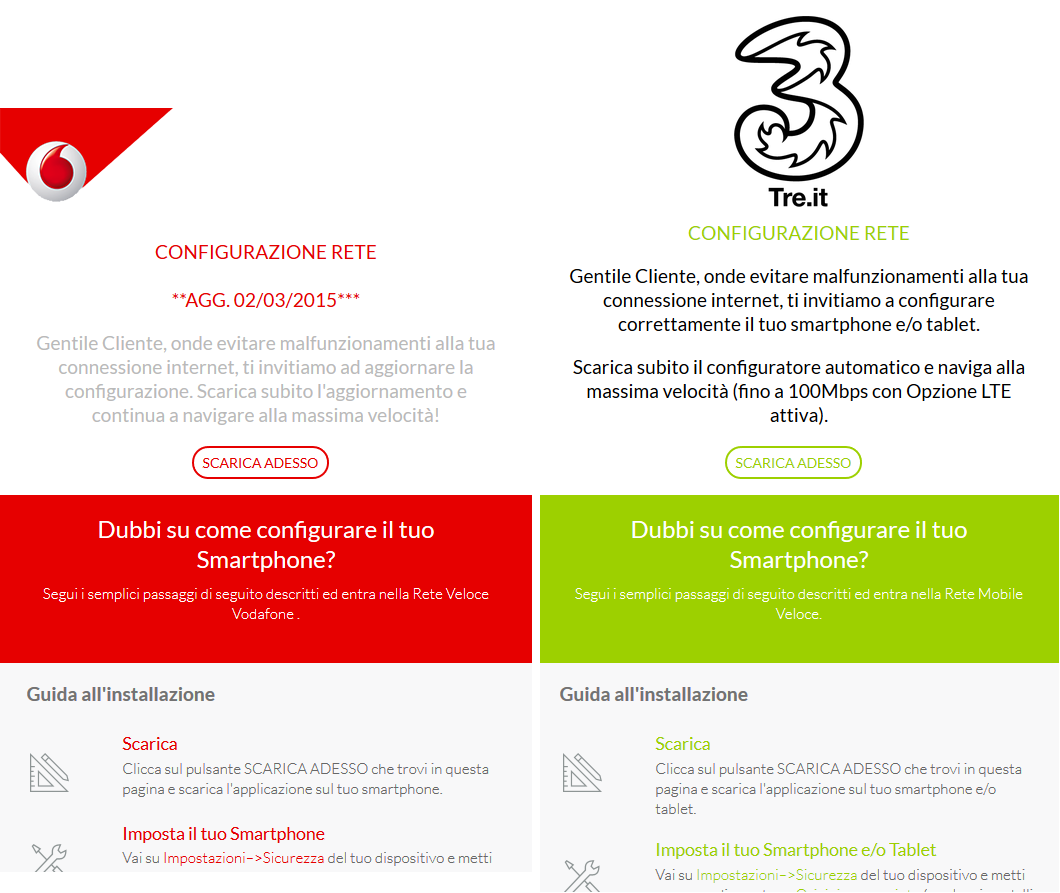
Kaspersky Lab said Tuesday the spyware has only infected a handful of users – all in Italy – meaning it’s not exactly a threat to the everyday Android user just yet. The fact that Skygofree has been developed slowly over the course of three years may portend the attackers behind the malware are in it for the long haul however.
The fact the collective behind Skygofree is purportedly Italian is prompting many in the security sphere to draw parallels to Hacking Team, an Italian information security company that made headlines several years ago for its controversial practices, namely selling its surveillance products to oppressive regimes, like Sudan and Ethiopia.
It’s possible – although unconfirmed – that Negg, a Rome-based IT firm that specializes in cybersecurity consulting and penetration testing is behind Skygofree. Kaspersky Lab didn't explicitly say Negg was made the spyware but did note it observed several references to the company's name in its code. WHOIS records and IP addresses point to “negg.” Several command and control servers point back to Negg sites, like negg.ddns[.]net andf negg1.ddns[.]net, as well.
A email request for comment to the company on Kaspersky Lab's research was not immediately returned on Tuesday.
A Forbes article published on Tuesday about Skygofree cited two sources "with knowledge of the Italian surveillance scene" who presumed the company was behind the spyware.
"They're working with the police now, I presume filling the gap left behind by Hacking Team at this point," one source told the publication.
