NIST SP 800-171 is an important set of guidelines that aim to ensure the safety and confidentiality of sensitive federal data. Here’s a look at what NIST encompasses and what’s required of affected entities.
Definition of NIST SP 800-171
NIST SP 800-171 is a document of guidelines published by the National Institute of Standards and Technology (NIST) in 2015, with compliance required as of December 31, 2017. The purpose of the guidelines is to “ensure that sensitive federal information remains confidential when stored in nonfederal information systems and organizations.” Enforcement of these regulations is handled directly by the Department of Defense, making compliance absolutely mandatory.
There are unavoidable occasions where federal data (any data related to the federal government) is held or received by third parties. Contractors and executive agencies who aid federal agencies commonly store or transmit sensitive data. These cases are regulated by NIST SP 800-171.
Cyber threats are ever-increasing and becoming more sophisticated. For this reason, the NIST guidelines have been revised a number of times. In fact, the initial version was replaced by NIST SP 800-171 Rev. 1. “Rev 1” has since been updated three times. It’s current version (as of this article being written) was updated on June 7th, 2018.
What Does NIST SP 800-171 Rev. 1 Cover?
The NIST document sets security regulations in 14 different categories, including:
● Access Control
● Awareness Training
● Audit and Accountability
● Configuration Management
● Identification and Authentication
● Incident Response
● Maintenance
● Media Protection
● Personnel Security
● Physical Protection
● Risk Assessment
● Security Assessment
● System and Communications Protection
● System and Information Integrity
All of these categories and regulations are to protect controlled unclassified information (CUI). CUI is federal data that is not classified, yet still sensitive. For instance, the U.S. government uses terms on certain sensitive data such as, “for office official use only.” While not classified, this designation means that the information is not meant for public consumption.
NIST SP 800-171 Requirements
Dozens of requirements are outlined across the 14 different categories. For instance, access control requires:
● Maintaining a list of authorized users
● Stating the roles and functions of all users
● Limiting permissions where possible
● Enable auditing
These are just a few of the requirements that fall under access control alone. However, all regulations outlined in NIST SP 800-171 can be summed up in two broad categories — administrative and technical.
whitepaper A Data-Centric Approach to Federal Government Security |
Administrative Requirements
These are the regulations that must be maintained and implemented by individuals, contractors, and executive agencies who deal with CUI. Many of these items include reviewing procedures, reading reports, and reporting vulnerabilities/incidents. To continue with the access control example, affected entities must review audited events annually (according to SP 800-171, control number 3.3.3).
Other measures include physical protections. These requirements include everything from the hardware (e.g., servers) to the buildings in which data is kept. Things as basic as locks on the doors and procedures for handling guests within an establishment are covered in the documents guidance.
Technical Requirements
With much of the data being in digital form and transmitted over the Internet, there are requirements that denote the need for technological solutions. These technologies are to create the reports, limit the access, and create digital security. Many organizations will have to employ third-party help of their own to create, implement, and comply with these requirements.
A large number of the technical requirements are to monitor, prevent, and warn organizations. Things like digital loss prevention, threat protection, data controls, and many more technical requirements exist in SP 800-171. Below is an image provided by NIST that illustrates such protections.
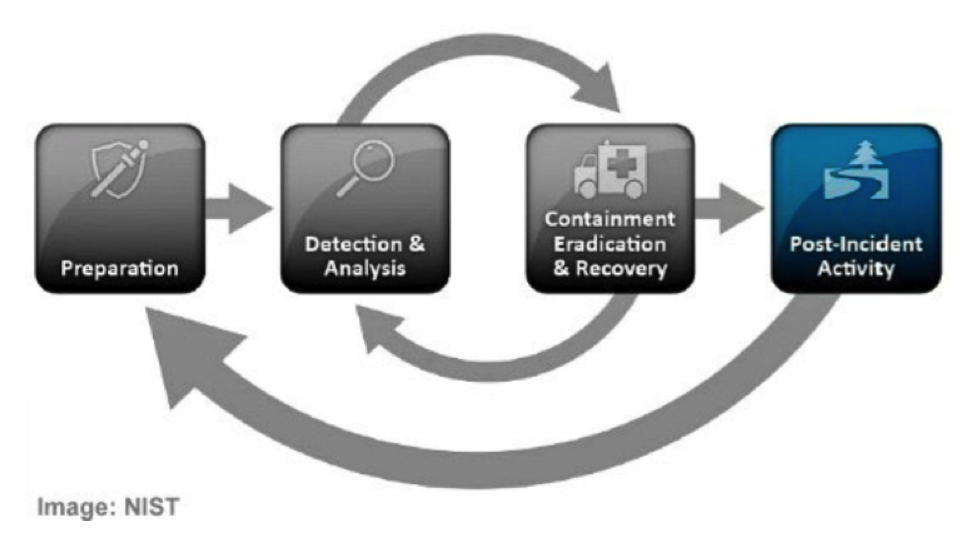
Let’s quickly break down each component listed in the image:
- Preparation: This would include things like proper onboarding of individuals who will have access to CUI data. Proper implementation of technology and software is a critical piece of preparation.
- Detection & Analysis: Analysis can fall under both administrative and technical requirements. Software can analyze data in order to detect threats and individuals can analyze reports provided by software.
- Containment, Eradication & Recovery: In the event of an incident (breach or loss of data), there are steps to take. These include containing/closing the incident, eradicating the vulnerability that led to the incident and recovering lost data (where possible).
- Post-Incident Activity: Once the incident has been contained, there are certain things that must take place. Agencies must be notified and reports must be filed.
Once all incident activity has been properly handled, lessons learned from errors made can be implemented to better prepare and guard against future threats. From the administrative standpoint, a correction of errors should be made by all parties involved. On the technical side, changes to hardware and software may be necessary.
NIST SP 800-171 is a broad set of guidelines and requirements that aim to ensure the integrity of sensitive federal data. But these regulations are of concern to more than just government entities; it’s imperative that any entity that receives, transmits, stores, or otherwise comes into contact with covered data complies with these requirements.
