FBI Highlights Increase of BEC Exposed Losses
| Contact Us | |
| Free Demo | |
| Chat | |
New numbers claim there was a 65% increase in identified global exposed losses connected to BEC scams from 2019 to 2021.
It seems the severity of business email compromise (BEC) scams can't be overstated. The attacks, which accounted for $2.3 billion of the $6.9 billion lost by Americans to cybercrime last year, continue to evolve, according to the Federal Bureau of Investigation.
New numbers, released late last week, revealed that between July 2019 and December 2021, there was a 65 percent increase in global losses to BEC scams. The number, which corresponds to a potential $43 billion lost, is based on financial data reported to the FBI's Internet Crime Complaint Center and includes dollars that were actually lost and dollars from BEC attempts.
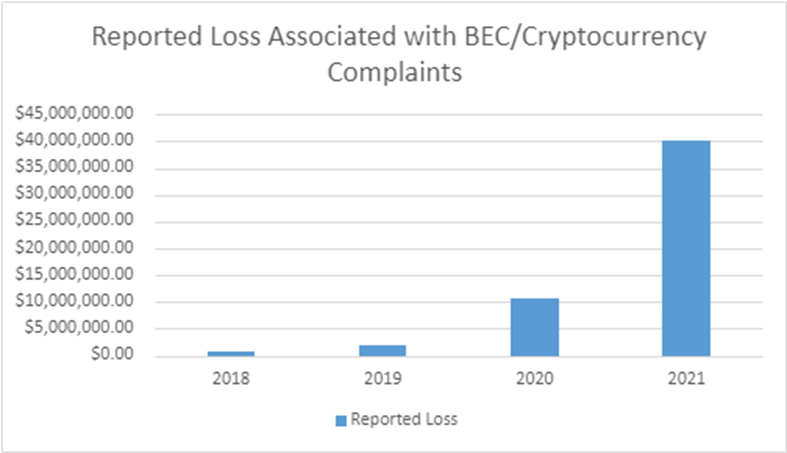
BEC scams can have a serious financial toll on businesses if successful. They traditionally involve using a combination of social engineering and hacking to trick employees into either performing a wire transfer for the attacker or surrendering valuable personally identifiable information (PII).
One variation the FBI claims it’s seen a lot of lately involves cryptocurrency wallets. In one, after taking control of a wallet for the funds to be distributed to, the cybercriminals convinces the victim to deposit money to a cryptocurrency exchange. In another, dubbed a second hop transfer, the cybercriminals rely on victims of other scams. Taking information obtained from those scams, the attackers open cryptocurrency wallets in their names that the attackers can still access and cash out.
When the money is rerouted, it usually goes through banks in Thailand and Hong Kong, according to the FBI. China, which has long been the primary destination of fraudulent funds, was the third most popular destination last year.
To combat the issue, authorities are advising businesses to be more alert in general.
Just as one should do before clicking through a link or opening an attachment in a foreign looking email, at risk employees should double check suspicious looking requests for account information like login credentials or anyone seeking PII. They should also be on the look out for hyperlinks that misspell the actual domain and that the URL in emails match the business it claims to come from.
Those in charge of financials at organizations should regularly monitor their accounts for missing deposits, as well.
Using a combination of authentication, employee education, and encryption can go a long way in protecting your business as well.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.
