How to Protect Data and Defend Against State-Sponsored Hackers
| Contact Us | |
| Free Demo | |
| Chat | |
NIST has released new tools for defenders to protect sensitive information and mitigate state-sponsored hackers.
Between coordinated attacks on the healthcare industry, last month's massive SolarWinds supply chain hack, and repeated attempts to steal U.S. financial and intellectual property, nation state hackers have been behind a substantial chunk of attacks over the last several years.
Of course, hackers working on behalf of a foreign government - the People's Republic of China and Russia especially – have long been adversaries to the US. Lately however, the ability to purchase cyber tools and a low barrier to entry has led to widespread damage and as a result, reshaped how nation state attackers fit into the cyber threat landscape.
While some entities, like federal agencies that deal in trade secrets and confidential data, have battle plans in place to mitigate state-sponsored hacking, not every organization may have the right plans in place.
To aid these organizations in securing systems from advanced persistent threats from state-sponsored hackers, the National Institute of Standards and Technology (NIST) this week released new tools in the form of Special Publication 800-172.
The document, Enhanced Security Requirements for Protecting Controlled Unclassified Information, is designed to help protect sensitive federal information on nonfederal systems that may not have as rigid data protection policies as a federal system.
NIST gives a few examples of such data, they run the gamut from sensitive information about people, technologies, innovation, and intellectual property; information that if compromised, could impact the country’s economy and national security.
Administrators, CIOs, and auditors who oversee systems at state and local governments, academia like colleges and universities, and independent research organizations like think tanks – basically any organization that works tangentially with federal programs and may parse federal data – should consider reviewing and implementing the guidance.
In addition to SP 800-172, NIST is encouraging organizations to review SP 800-171 – first published last February, of which SP 800-172 is a supplement - for further guidance on mitigating attacks
The difference between SP 800-171 and SP 800-172 is that the latter is designed to help administrators drill down on safeguards in place to ensure the confidentiality, integrity, and availability of government created or owned data, technically Controlled Unclassified Information, or CUI. SP 800-171 is only designed to ensure the confidentiality of such data.
The latest report includes enhanced requirements to protect the CIA of CUI from APTs like access control, awareness and training, incident response, and maintaining a form of security assessment, like penetration testing or automated scanning tools.
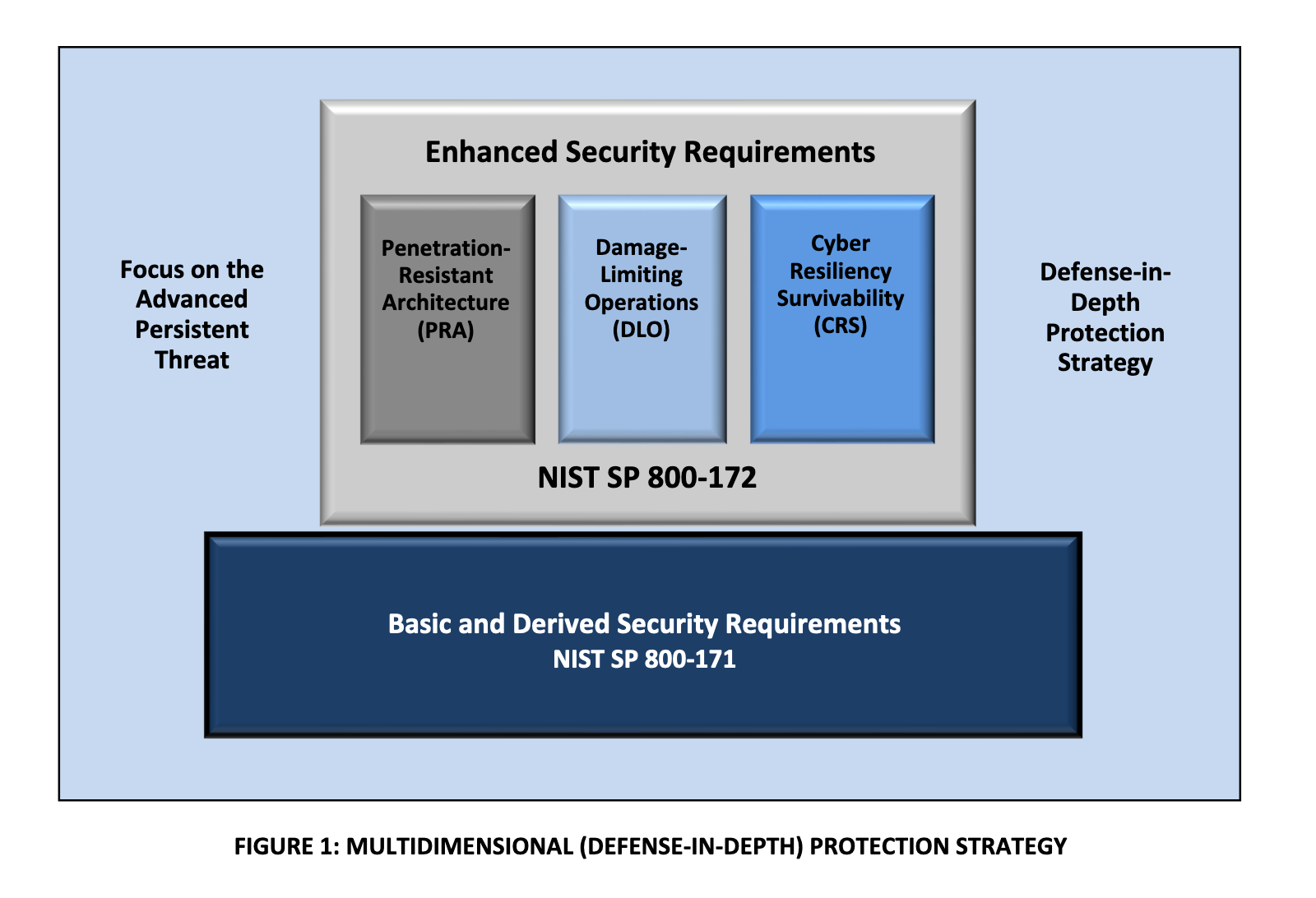
Not all of the NIST's guidelines are going to apply to an organization. Federal agencies will have to select a security requirement, complete the requisite assignment and selection operations, develop implementation guidance, and include the requirement and implementation guidance in federal contracts to demonstrate proficiency. Essentially, administrators will want to go through the report, line by line, to identify how each can benefit their organization.
“Most likely an organization implementing this guidance will not want to use all of the enhanced security requirements we offer here,” Ron Ross, a computer scientist and a NIST fellow said this week. “The decision to select a particular set of enhanced security requirements will be based on your mission and business needs — and then guided and informed by ongoing risk assessments.”
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.
