Strengthening Your Human Firewall through Ongoing Security Training and Guidance
| Contact Us | |
| Free Demo | |
| Chat | |
Educating end users is a process, not an event
We’ve all participated in security training events. This can be as simple as reading and acknowledging your corporate information security standards, or taking an “Introduction to Security” eLearning course. The long-term success of these, to nobody’s surprise, is minimal. You don’t learn to drive a car by attending a drivers’ education seminar, or become fluent in a new language by listening to a single language learning lesson. Similarly, you don’t retain security knowledge without repetition over time.
This fact has been studied many times. The graph below, from the University of Waterloo, is representative. People begin to forget information learned almost immediately after a lesson. By the end of a week, a typical student can recall only 10% - 20% of the information from the lesson. The yellow line represents reduced “forgetting” when the information is reinforced (reviewed) for short periods over the first 30 days. Now, instead of retaining 10% of the information from the lesson, the student retains 80%-90% of the information.
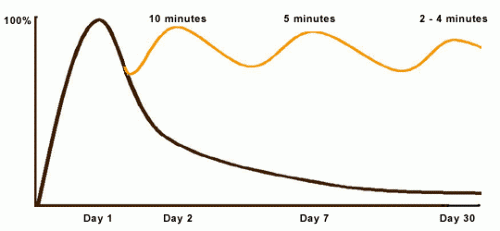
The Curve of Forgetting, University of Waterloo Consulting Services
It turns out that the “secret” to successful training is no secret at all; schools have used the methods for years. Learning a new skill takes time, feedback, and repetition under a variety of scenarios. If you want to learn French, you could adopt the Rassius Method, which emphasizes interactive drills and repetition. If you want to become a better tennis player or golfer, you practice. If you have a coach, she might take videos to point out foot position and the mechanics of your swing.
The same rules apply to learning new business skills, including information security. I’m not suggesting that companies send employees to weeks of training classes, but time, feedback and repetition are still required. The trick is to build training into the everyday business process, so employees receive consistent, ongoing reinforcement on the use of sensitive data while they work.
Knowledge workers are busy, and security may not always be top of mind. Some organizations address this with posters or notes on whiteboards (e.g., “please erase all notes before leaving this meeting room”). Others will run periodic internal tests for social engineering lapses, such as seeing if people click on links in a spoofed email, and then publicizing the results. Prompting users about policy as they are performing a task that could put information at risk is the ultimate goal. We can already do that with password selection, by requiring a specific level of complexity.
Training users on security is no different from training people on any other subject. The important part is recognizing that you cannot do it in isolation. Learning is a process, not an event.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.