Employees send emails, create documents, and upload files to internal servers and cloud applications every day, and the volume of data is growing exponentially. How can you ensure that sensitive data remains secure without burdening your end users with time-consuming and confusing workflows?
Fortra's Data Classification (formerly Titus and Boldon James) and Digital Guardian Secure Collaboration (formerly Vera) integrate to provide an end-to-end solution that helps organizations find, categorize, secure, and track the data they have. Data classification, combined with encryption, secure collaboration, and data protection, enables employees to work and collaborate more freely, both internally and externally, without having to worry about understanding what is or is not confidential and what needs to be encrypted.

The Challenges
In today’s distributed enterprise, data is everywhere: within on-prem share drives, in the cloud, on desktop devices, and on employees’ mobile devices. So, understanding what data you have, and where it’s located, has never been more difficult—or more important. This becomes even more critical if that data is sensitive.
But how do you define what data is sensitive and what isn’t? Almost anyone knows that personal information such as social security numbers, addresses, phone numbers, insurance numbers, personal health data, or bank account numbers is confidential. However, when it comes to company-specific information like business plans, product roadmaps, design files, product documentation, and intellectual property, it isn't always as straightforward.
This type of information typically presents the greatest challenge for organizations to deal with. Categorizing and protecting this data proactively, consistently, and accurately compounds this challenge, as failure to do so represents a real security risk. Likewise, context is crucial for accurate data classification and in the end, the most effective way to keep information protected is to employ a strategy based on a combination of people, processes, and technology.

Data Classification: The Foundation of Effective Data Protection
Data classification is an integral part of the Information Lifecycle Management (ILM) process—so much so that data classification is often considered the foundation of any data security solution, both within the corporate firewall and in the cloud. Employees can’t protect their organizations' data when they don’t know enough about the contents of files to handle them properly.
Once a user has created a file or an email, a classification solution scans the file to accurately identify the sensitivity of the data and applies visual labels and metadata that can be read by the entire security ecosystem. Then, a policy engine determines what actions to take. The classification process can be guided (asking the user to confirm the recommended classification level), automated (applying the classification level automatically, without user input), or simply done manually.
Not only does data classification provide organizations with the ability to make more intelligent and conscious decisions about how data is used and handled, but in an age of growing regulatory compliance requirements, it is a critical tool in demonstrating compliance now and remaining compliant in the future.
Secure Collaboration Enables Control Over Your Most Sensitive Data
Secure collaboration solutions enable organizations of all sizes to protect their sensitive data by encrypting the file and then providing the ability to track, audit, and manage the policies securing the data anywhere it goes. So, confidential data stays protected no matter what device, person, cloud, or application it travels to.
Most importantly, a secure collaboration solution will ensure that your sensitive data is protected even when it travels outside of your organization. This is a must for industries or job functions (e.g., financial or legal) that frequently require external collaboration with information that would be highly detrimental to the organization if a breach were to occur. Should data fall into the wrong hands, either accidentally or maliciously, this tool will allow you to revoke access to the file in real time.
In today’s hyper-competitive business climate, the ability to maintain control of your data, manage who can access and modify your sensitive files, and track your intellectual property is critical. Secure Collaboration provides the peace of mind that your security policies will stick with your most important data.

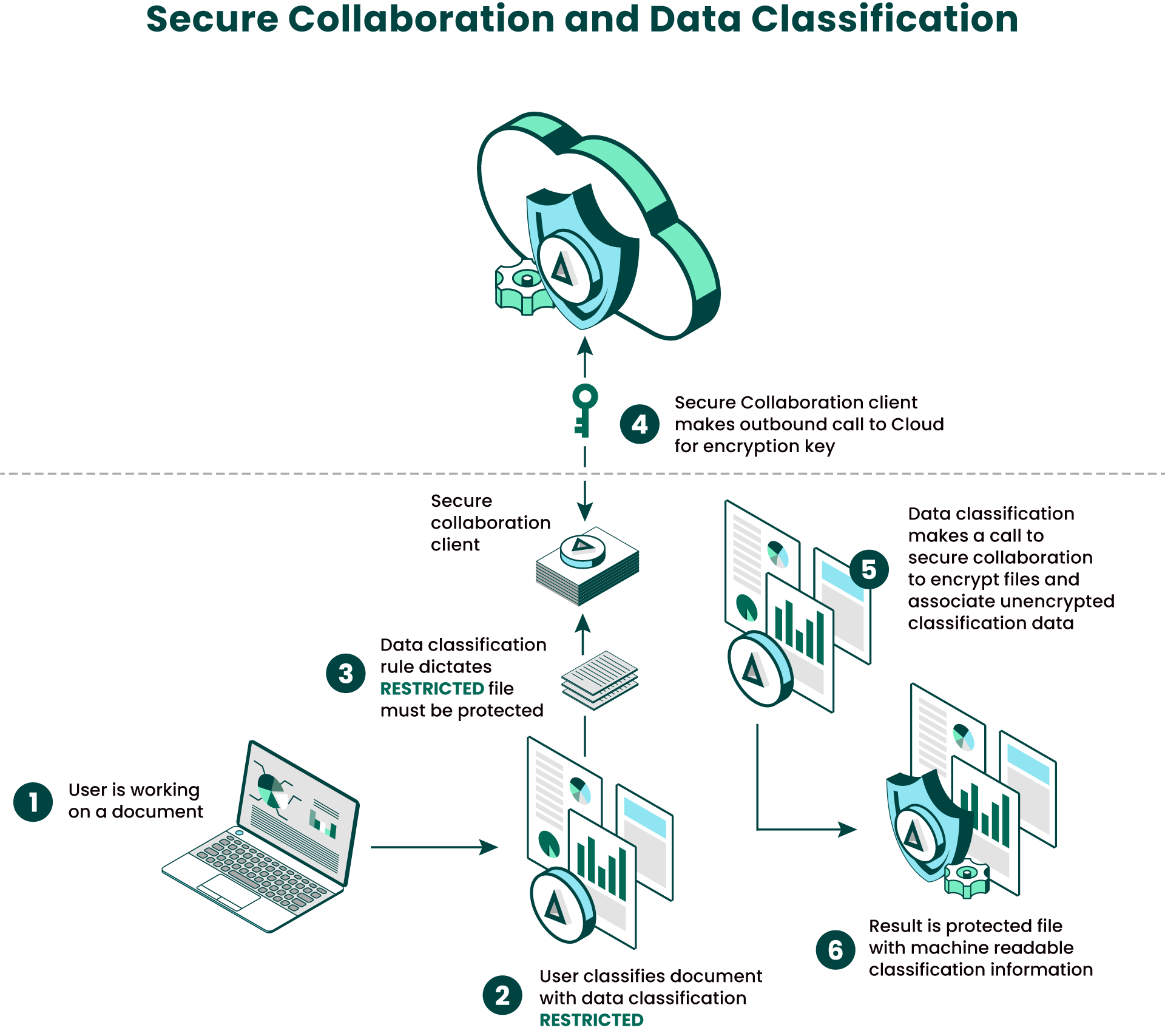
How It Works
For example, an organization may have a security policy mandating that all sensitive files must be classified before they can be shared via email or cloud.
In this scenario, once a file is tagged with a “Restricted” classification, it is then considered secured. The file is encrypted and access controls are added along with any other specific policies tied to that “Restricted” classification. Unencrypted classification metadata is embedded in the header of the secured file, resulting in a protected file with machine-readable classification information.
Therefore, while the file is now encrypted, other security tools like data loss protection software (DLP) or a cloud access security broker (CASB) can still read the metadata containing the classification value.
Benefits
Together, these solutions employ a powerful combination of best-of-breed classification and file-level security, helping organizations better understand and categorize their data while simultaneously securing it wherever it travels. This not only facilitates smoother workflows, but also dramatically improves organizations' overall security postures, helping to protect against data breaches and sensitive data falling into the wrong hands.
Moreover, both technologies complement other security solutions used to protect data at rest and the flow of data, such as CASB and DLP. And since both solutions are part of the Fortra Data Security Suite, you gain the advantage of working with a single vendor for all your data-centric security needs.
Integration Overview
Get Started Sharing Sensitive Files
See our secure collaboration solution in action for yourself.



