Zero Trust has been one of the cybersecurity industry's favorite buzzwords for a few years and for good reason; it's emerged as a legitimate strategy that—assuming the correct groundwork is laid—can help effectively guard against threats and strengthen an organization’s security posture.
What is Zero Trust?
Zero Trust is rooted in the idea that everyone is a threat until proven otherwise. Only once a user’s access level is verified, either via multi-factor or two-factor authentication, can they be granted access. With zero trust, networks are segmented into groups that require their own access. This ensures that if an attacker were to infiltrate one network, they wouldn't be able to access them all.
Lost in the chatter around zero trust is how integral data classification is to the equation. For a zero trust framework to work correctly, it's critical that organizations know where their sensitive data is located, when it's created, how it's used, shared, and, in particular, who's accessing it: that's where data classification comes into play.
Data visibility has long been a challenge for organizations. Not knowing where your data is can make it nearly impossible to protect it from loss and even harder to comply with privacy regulations such as HIPAA’s Privacy Rule, PCI DSS, and the CPRA that mandate that data containing certain types of information be handled with specific safeguards.
With a data classification solution in place, organizations can determine where data resides in their ecosystems, apply sensitivity-based access control guardrails, and then parcel out access based on the data’s sensitivity level. According to Forrester, there are two foundational steps to achieving Zero Trust compliance:
- Having a mature data identification and classification framework in place.
- Having strong identity and access management.
Which Approach Is Right for Zero Trust?
While there are three types of data classification that are viewed as industry standard, one is more helpful than the others when it comes to implementing a zero-trust framework:
Content-based Classification
Inspects and interprets files, looking for sensitive information.
Context-based Classification
Looks to the application, location, metadata, or creator (among other variables) as indirect indicators of sensitive information.
User-based Classification
Requires a manual, end-user selection for each document. User-based classification takes advantage of the user's knowledge of the sensitivity of the document, and can be applied or updated upon creation, edit, review, or dissemination indicators of sensitive information.
With context-based classification, an organization can identify, classify, and provide critical context to data, something that can be used to create visual and metadata labels to organize data by type and sensitivity.
This metadata can be leveraged across your data security ecosystem and can add accuracy to downstream data protection tools you may already use, like data loss prevention (DLP), access management, and cloud access security broker (CASB) solutions.
The Four Categories of Data Classification
Typically, there are four ways to categorize data:
Public
Data/information that is freely used, reused, and redistributed with no restrictions on access or usage. Examples: press releases, brochures, and published research.
Internal
Data that is strictly accessible to internal employees/personnel who are granted access. Examples: company memos, internal communications, and marketing research.
Confidential
Data that requires granted access and/ or authorization and should be contained within the business or specifically permissible third parties. (E.g., personally identifiable information, intellectual property.)
Restricted
Data that is highly sensitive with use limited on a need-to-know basis. If compromised or accessed without clearance, this could result in criminal charges, heavy legal fines, and irreparable company damage. Examples: trade secrets, PII, health information, and data protected by federal regulations.
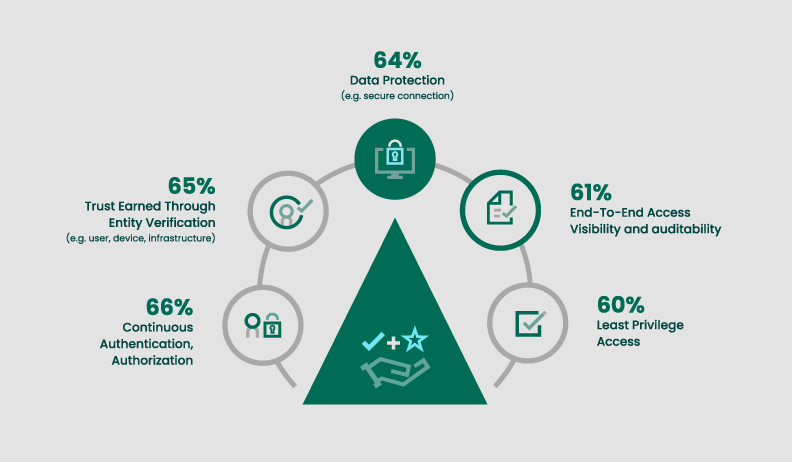
Fortra and Cybersecurity Insiders collaborated on a Zero Trust security report, asking 400 cybersecurity professionals what the most compelling tenet of implementing Zero Trust is. 64% of respondents said data protection.
Take It One Step Further: Sensitivity Tags
Further context can also help organizations segment data based on its risk sensitivity.
If your data was compromised, what would the damage be?
Data Classification and Zero Trust Go Hand in Hand
Without data classification labels and context, zero trust models wouldn’t know how to check permissions around who can and can’t access certain data and, in turn, provision access.
For some organizations, it's not just who can access what. It's who accessed what. By being able to trace back what's been accessed, organizations can get a clearer picture as to how data is being handled behind the scenes, another benefit of data classification.
Zero trust requires a robust portfolio of security solutions to work; access control only solves part of the problem. Thankfully, the context around data provided by classification can also help inform:
Identity Management
Firewalls
Automation & Orchestration
Device Security
Workload Security
Threat Analysis
If you’re in charge of securing data at your organization, you already know that classifying it is foundational for data security. It’s especially the case for organizations looking to take a zero-trust approach to data protection.
Organizations serious about getting started on their zero trust journey should prioritize creating a data classification framework to determine what sensitive data they have, then classify it by sensitivity level.
Start With Fortra Data Classification
Fortra Data Classification adds rich context to your data, allowing downstream security solutions like Fortra Digital Guardian DLP to do their job better, with less friction, and across platforms and applications, meaning you'll gain full data visibility without interrupting your employees' workflows. Schedule a demo today to see it in action.