Twitter Urges All Users to Change Password Following Internal Bug
| Contact Us | |
| Free Demo | |
| Chat | |
The site says there's no evidence of a breach or misuse but that it's making efforts to prevent the incident from happening again.
Twitter urged more than 330 million of its users to change their passwords on Thursday after the company identified a bug, internally, that unmasked passwords in a log.
While the site claims there's no evidence of a breach or misuse, it reached out to users "out of an abundance of caution," late Thursday.
We recently discovered a bug where account passwords were being written to an internal log before completing a masking/hashing process. We’ve fixed, see no indication of breach or misuse, and believe it’s important for us to be open about this internal defect. https://t.co/BJezo7Gk00
— jack (@jack) May 3, 2018
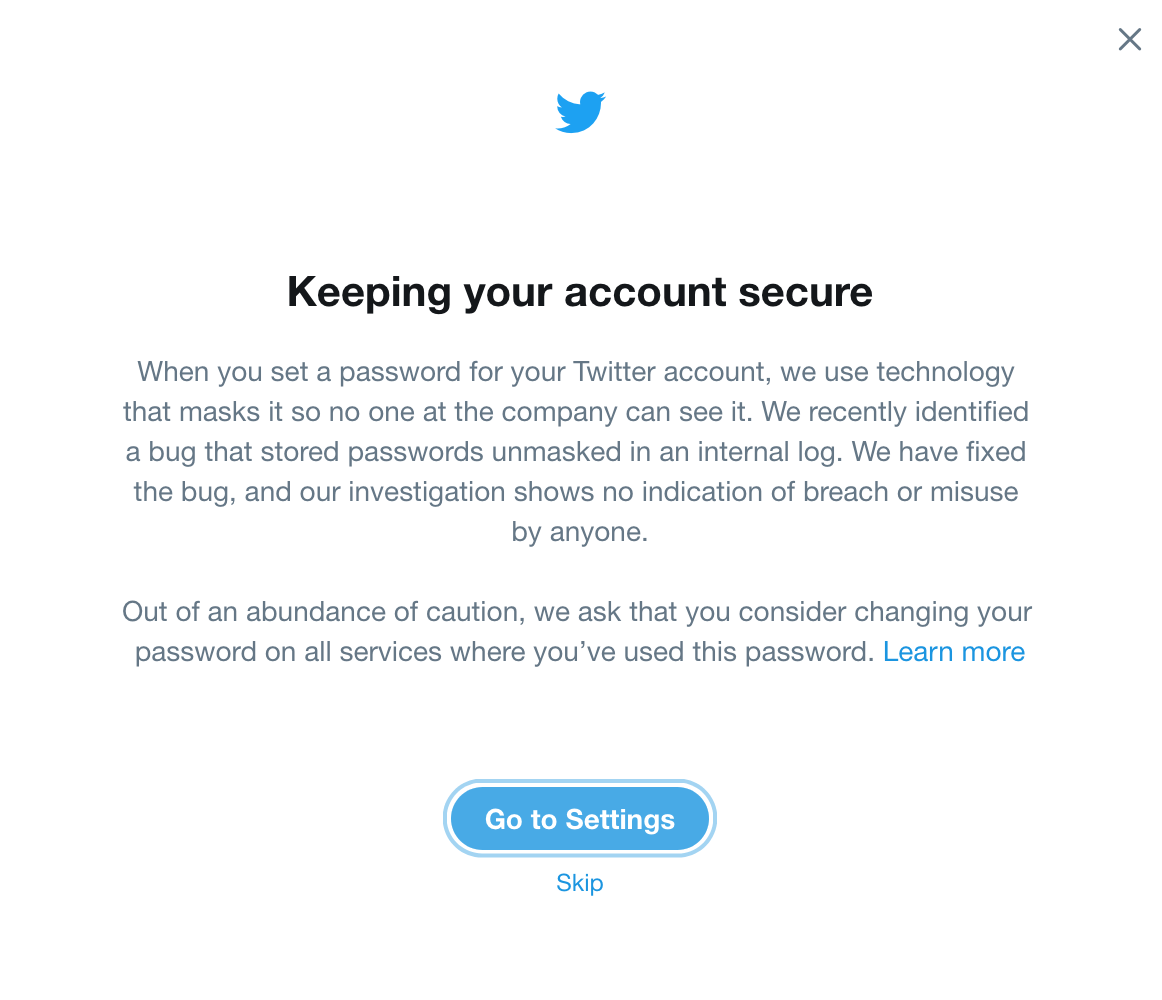
The service pushed an email to users alerting them of the issue but also displayed a pop-up notification upon logging into the service asking users to consider changing their password on Twitter, or any other service in which the same password was used.
According to Parag Agrawal, Twitter's Chief Technology Officer, a bug caused passwords to be written to an internal log before they were hashed with the popular password hashing function bcrypt.
“We found this error ourselves, removed the passwords, and are implementing plans to prevent this bug from happening again,” Agrawal wrote in a post to Twitter’s blog.
What remains unclear is how long the log was storing passwords in plaintext and how long it took engineers so long to notice. Twitter did not immediately return a request for comment on Thursday.
|
Blog Post 101 Data Protection Tips: How to Keep Your Passwords, Financial & Personal Information Online Safe |
It’s possible, as some users have speculated on Twitter, the site uses the same third party library/system as GitHub, another service that admitted this week an unspecified internal log bug exposed some users' passwords in plaintext.
"During the course of regular auditing, GitHub discovered that a recently introduced bug exposed a small number of users' passwords to our internal logging system," GitHub said in an email sent to users on Tuesday. Like Twitter, GitHub stressed in the email that it stores user passwords with bcrypt but that the "recently introduced bug resulted in our secure internal logs recording plaintext user passwords when users initiated a password reset," something that suggests the number of those affected by the GitHub issue is far fewer than those affected by the Twitter incident.
While the incident is a major gaffe and fairly large oversight on Twitter's part, several security experts, including the Electronic Frontier Foundation's Eva Galperin and Facebook's departing CSO Alex Stamos, noted the fact the company came clean about the incident shouldn't be overlooked.
This is one of the big problems holding back bug bounties from wider use outside of tech: companies believe they will be publicly crucified for acting responsibly and disclosing flaws even when not required.
— Alex Stamos (@alexstamos) May 4, 2018
Yes, you should change your Twitter password today.
Yes, it is good that Twitter was transparent about the problem.
Yes, I can think of some better ways to have handled it, but it’s not like I know what happened behind the scenes.— Eva (@evacide) May 4, 2018
It’s genuinely exhausting seeing Twitter get raged against for making a very, very hard call, correctly. Stop it, or nobody will ever do anything not aggressively legislated as a requirement.
— Dan Kaminsky (@dakami) May 3, 2018
Twitter users throughout the afternoon acknowledged the irony of the situation. News of the bug came on World Password Day, a holiday contrived by organizations to foster better password habits.
Recommended Resources

All the essential information you need about DLP in one eBook.

Expert views on the challenges of today & tomorrow.

The details on our platform architecture, how it works, and your deployment options.