LAS VEGAS – Buzzwords like machine learning and blockchain have mostly been the butt of jokes here at Black Hat but researchers have genuinely been able to use intelligence and data forensics to make a difference when it comes to processing vast swathes of information on the web.
Researchers with Terbium, a dark web data intelligence company and the Royal Bank of Canada, described this morning how they were able to use intelligence harvested from the dark web, alongside transactional data, to trace the history of payment card fraud victims.
Credit card fraud remains an enormously profitable venture for attackers, who manage to rake in $10 billion each year.
By analyzing compromised cards and building up candidate groups, the researchers said can determine the point of compromise, or at least make an informed inference as to where certain cards may have been hacked.
“It’s a classic big data problem,” Cathal Smyth, a machine learning researcher with the Royal Bank of Canada's Vanguard cybersecurity team, said in a Black Hat session Thursday morning. “Often a breach can affect a large number of clients with a huge number of transactions, but there’s still a degree of uncertainty. Trying to find the right combination of candidates [victims] is like trying to find a needle in a haystack.”
Blog Post Finserv Data Security: Key Concerns for Banks & Credit Unions |
What the researchers elected to do was light that haystack on fire, figuratively, at least.
In one instance the researchers found a breach – but the point of compromise was spread across 10 batches of data. It had a large impact on clients but it wasn’t entirely clear where the breach took place. All that could be deduced, based on the data, was that a large number of Canadians were affected.
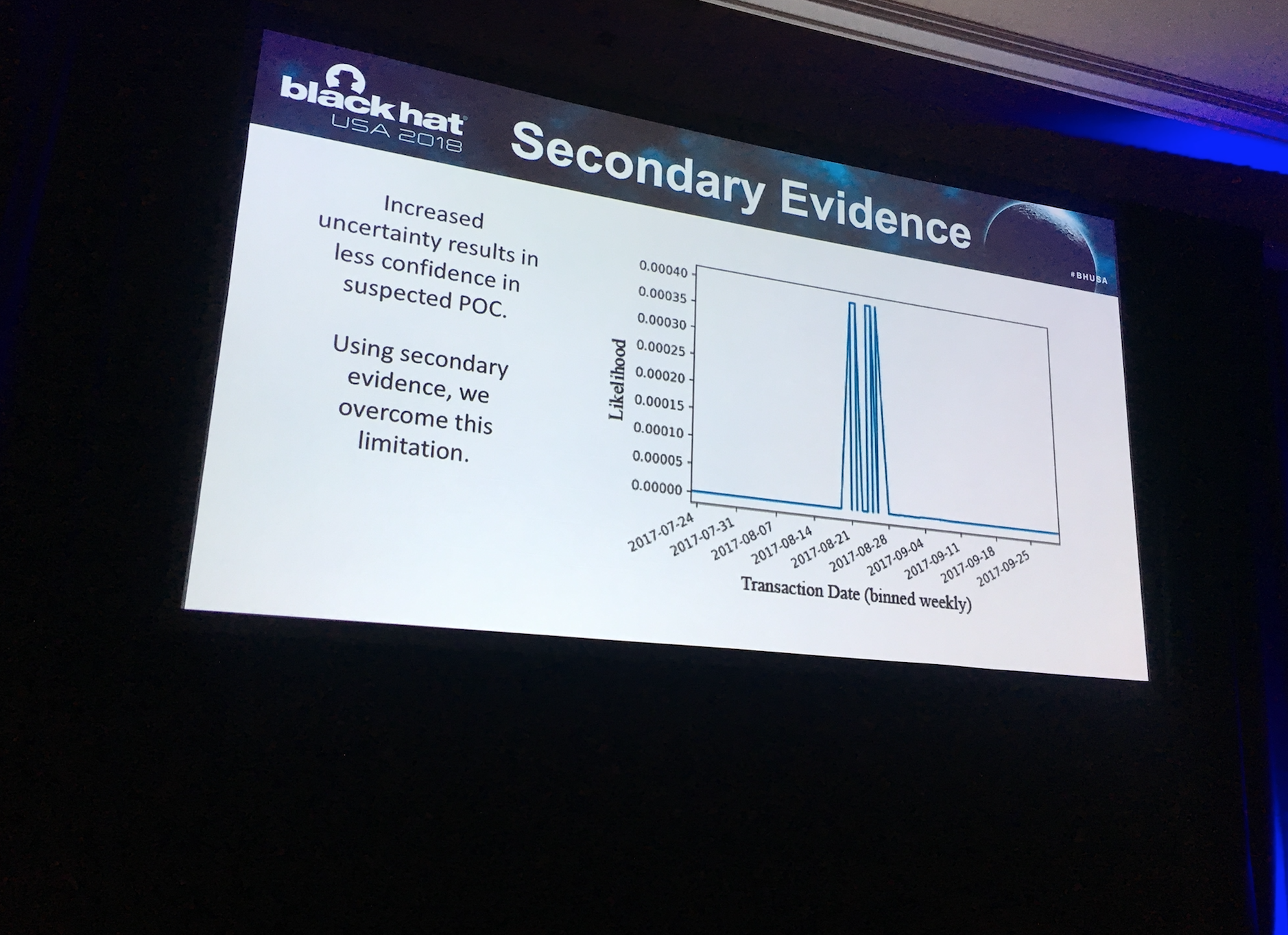
Eventually, after digging into the data, Smyth’s team saw transactions from a restaurant and a digital store, and observed an overlap between candidate transactions and the group, which confirmed a positive point of compromise.
One of the biggest challenges, as is to be expected, is interpreting all of the data.
"You can't assume there’s only one breach, you have to be careful with the thresholds you use but you can still make inferences," Smyth said.
Smyth and Clare Gollnick, Terbium’s CTO, said the process is a still a proof of concept but that it could be automated in time, to potentially identify victims in as little as 30 minutes.
The research is a bit like paleontology in the sense they’re going back, after fraud has happened, to identify accounts and systemic risk but could be adapted to help identify victims before fraudulent transactions have been made.
“Data is valuable and defense is necessary,” Smyth said, “using this approach it’s possible to prevent some sort of loss down the road.”

