Getting Started
Enjoy full data visibility and no-compromise protection with Digital Guardian, whether you manage it or we manage it for you.
Digital Guardian Deployment Options
Enterprise DLP needs enterprise class infrastructure. Add the option of dedicated cybersecurity experts to manage your program and you have world-class sensitive data protection.
Learn more about how Digital Guardian can make your data protection efforts more effective whether you manage it or we manage it for you.
- 24x7 Security Expertise
- Digital Guardian Solutions
- Back End Infrastructure
- Dedicatd Program Manager
- Professional Services
- Escalation & Ticketing Processes
- Digital Guardian Solutions
- Back End Infrastructure
- Support
- Professional Services
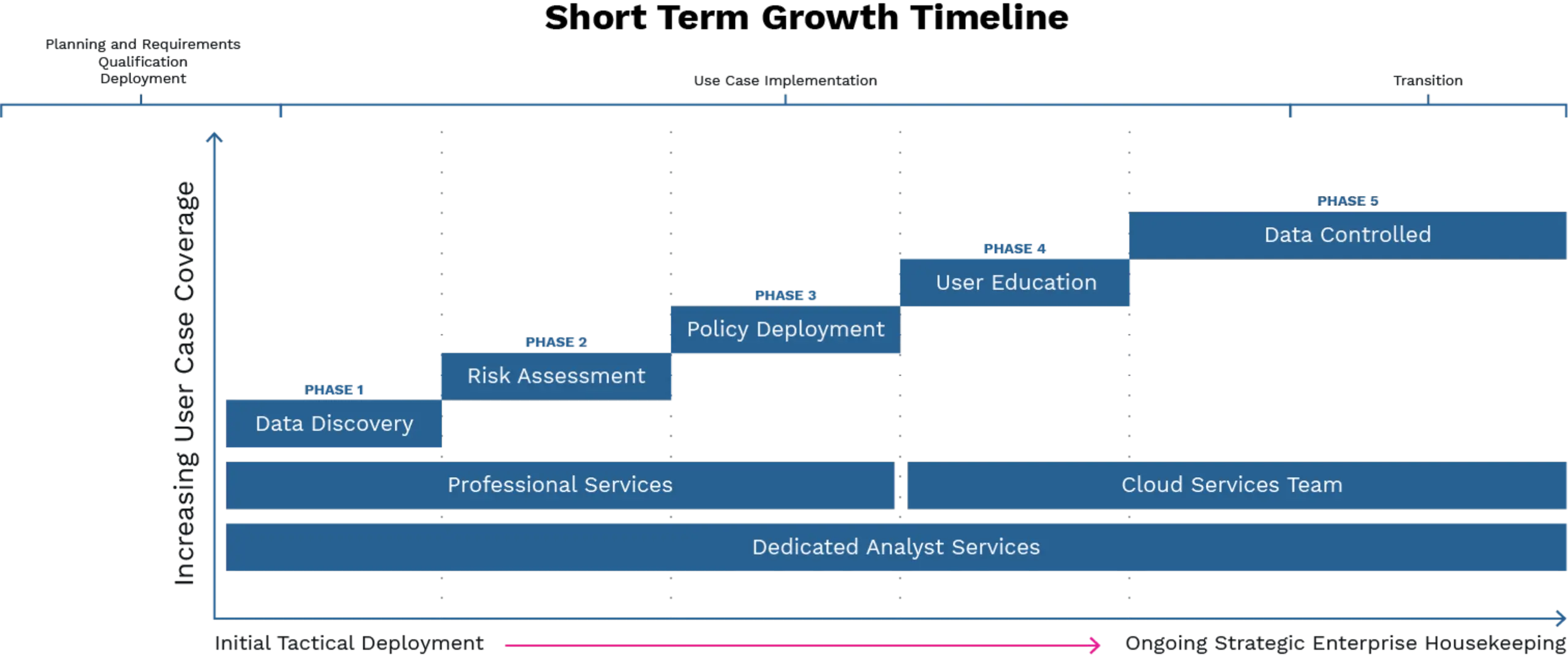
This is your timeline to implementing the Digital Guardian Managed Security Program.
PHASE 1
Data Discovery Goals
- Provides experienced Digital Guardian subject experts to help you pinpoint security & compliance risks.
- Documents the existence, scope, and severity of your data risks.
- Shows complete usage context from executive summaries to detailed forensics.
- Measures effectiveness of your current security policies and technology investments.
- Identifies how you can best take action on potential data threats.
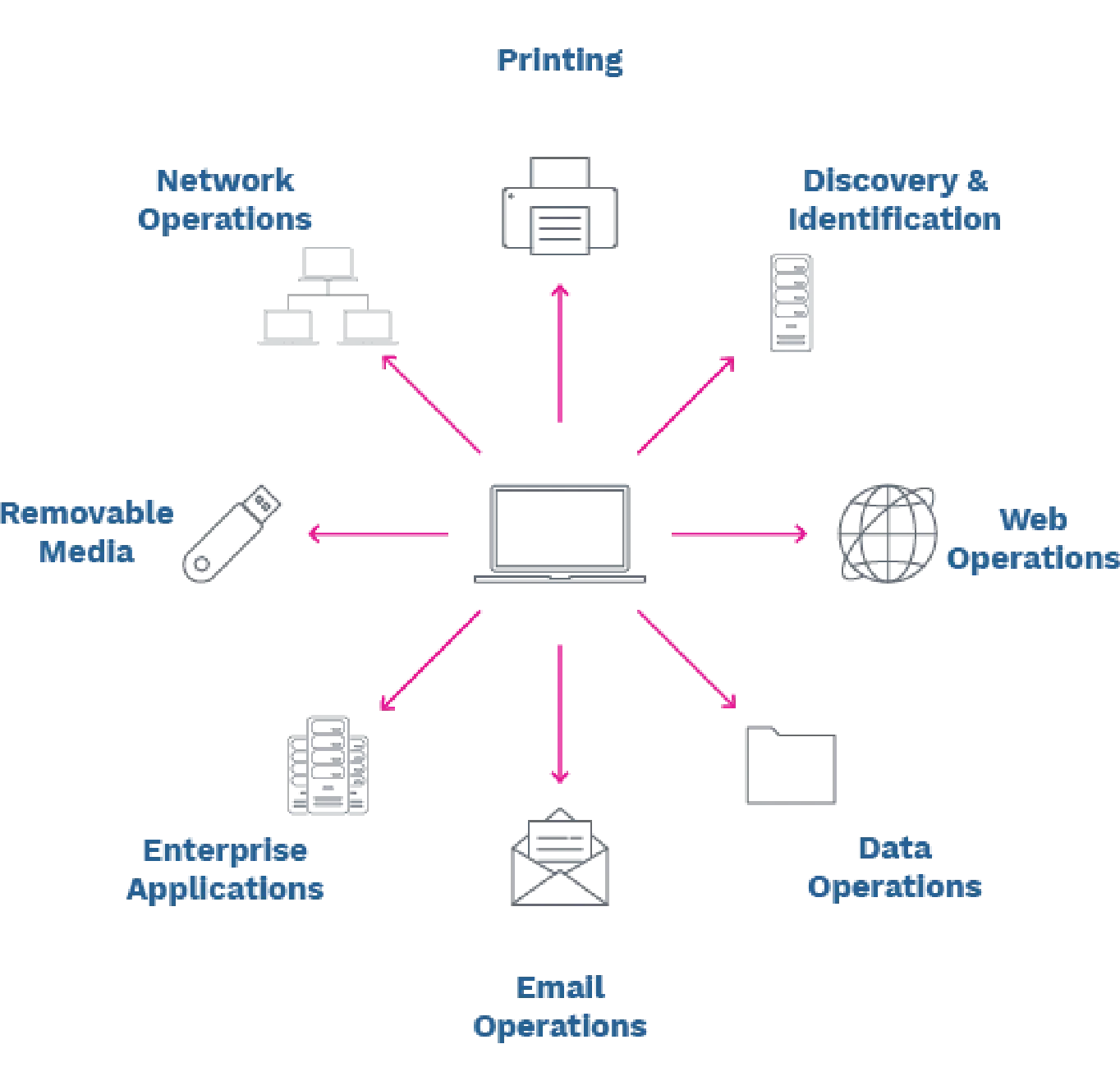
Our team of experts helps you locate and document where sensitive data lives and how moves in your extended enterprise. It’s often in places you don’t expect it to be, our experienced team can help you find it.
PHASE 1
Data Discovery Analytics
On demand and regularly scheduled overviews of activity.
Send Mail | NTU | CD/DVD | Removable | Copy & Paste | Print | Custom
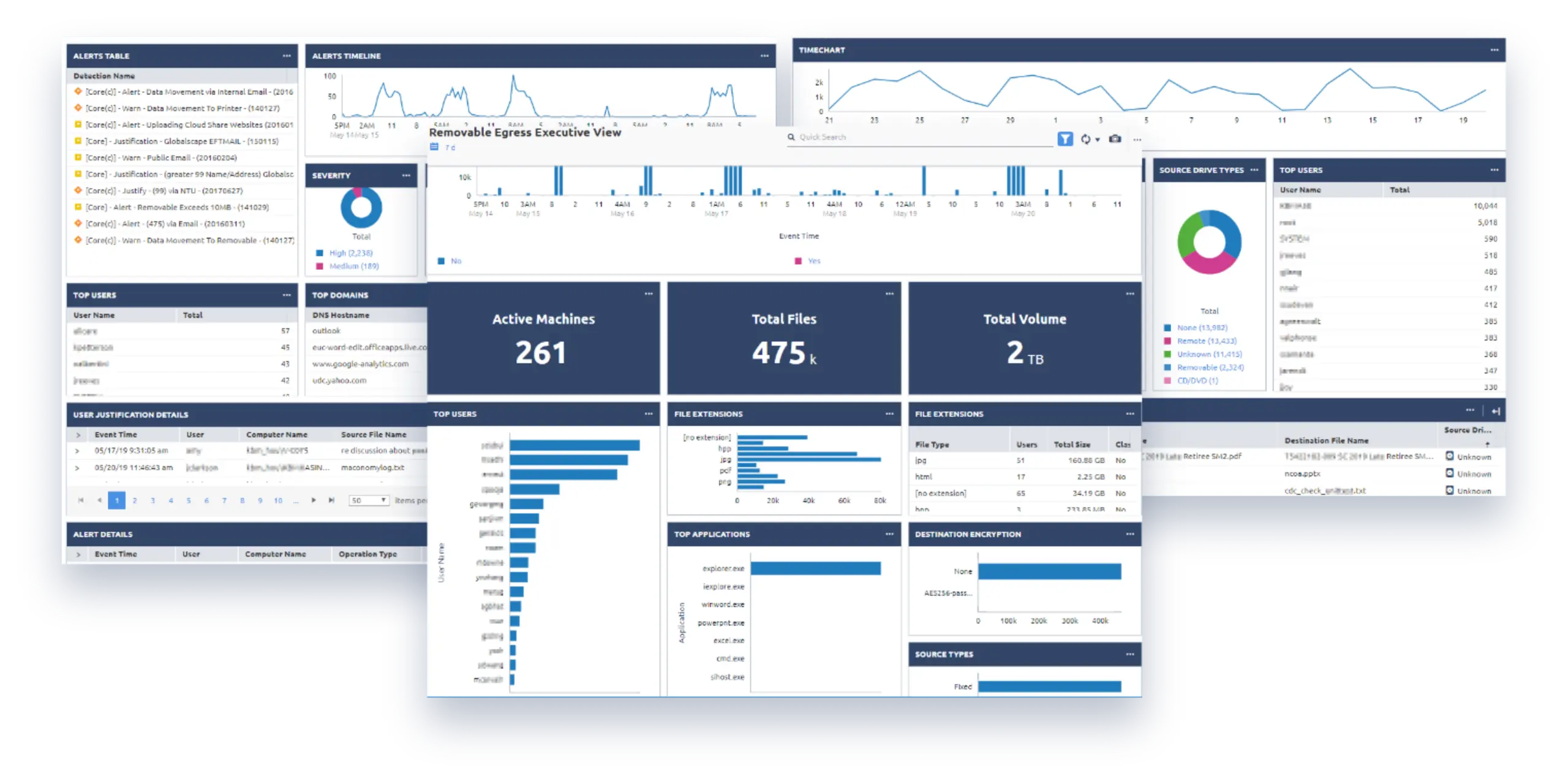
Our security experts will review your data footprints, showing you what data exists where and how they are moving. We’ll highlight any concerns we see and explain what it all means. Any urgent risks can be addressed here if needed.
PHASE 2
Risk Assessment Goals

With the data footprints documented our team will review with you the relative importance of the data and how it impacts your business if it were stolen or leaked. Is your primary focus on IP or regulated data? We can see and protect both, but prioritization based on business goals ensure alignment.
PHASE 2
Risk Assessment Methodology
Data Classification
- What constitutes sensitive information?
Data and Entity Inventory
- Where is it?
- How much of it is there?
Current Control Review
- How effectively is it protected?
Vulnerability Assessment
- What are the vulnerabilities that could lead to compromise?
- What is the likelihood of compromise?
Data Sensitivity and Risk Tolerance
- What is the potential impact?
Cost Benefit Analysis
- What is the most effective use of protection resources?
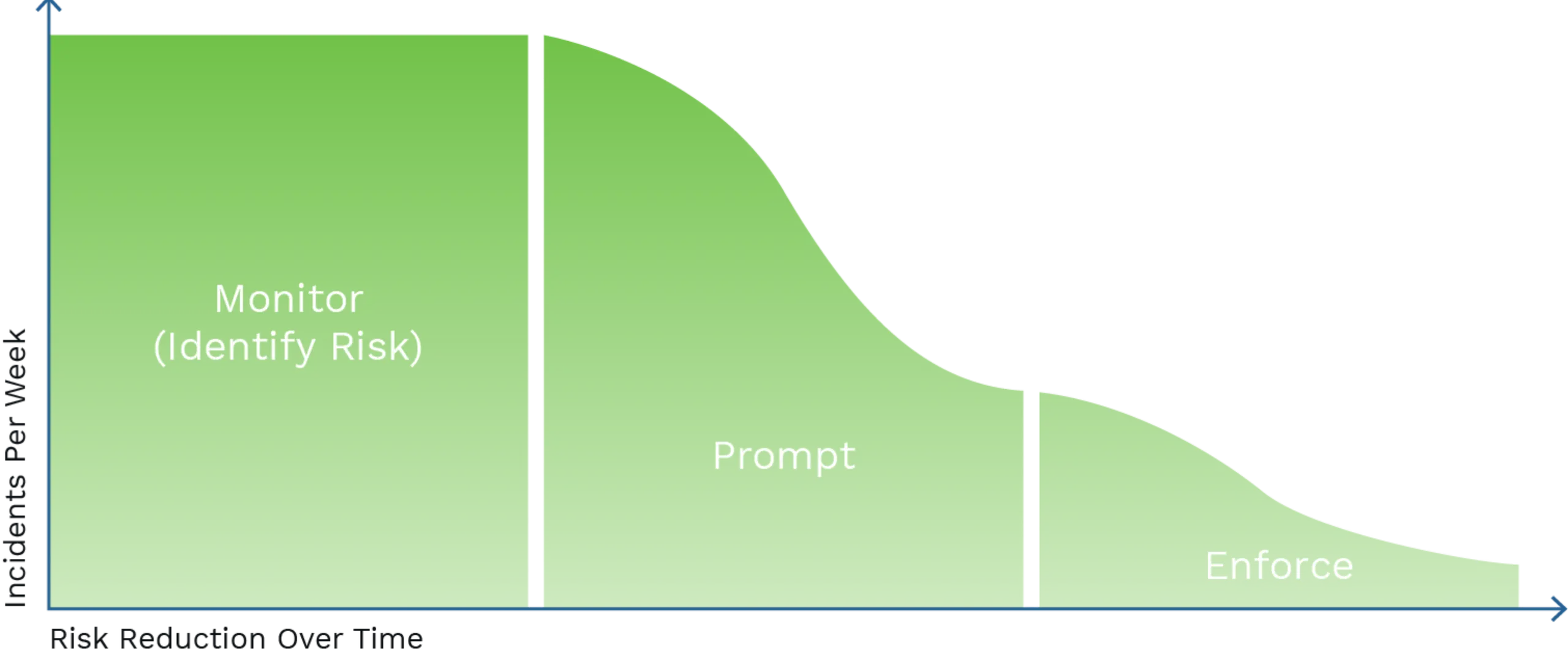
Our team uses this framework to document an overall risk assessment at the time of the initial data discovery and deployment. This serves as a place to start, we’ll use this baseline as your business evolves over time. Do your goals changes, does your risk profile change? All of this will inform an ongoing, and living risk reduction program, managed by Digital Guardian.
Going from limited visibility to the full visibility DG delivers can illuminate risks that were there all along, seeing them can be eye- opening. Your dedicated DG team will track the success of your data protection program over time, documenting the real improvements you will see.
The data discovery phase gives the DG MSP team the formula to create policies that match your business operations. These alerts will be reviewed and analyzed by our team to refine the policies as needed.
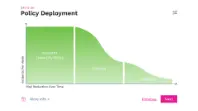
PHASE 3
Policy Visibility
Incredible insight on day one
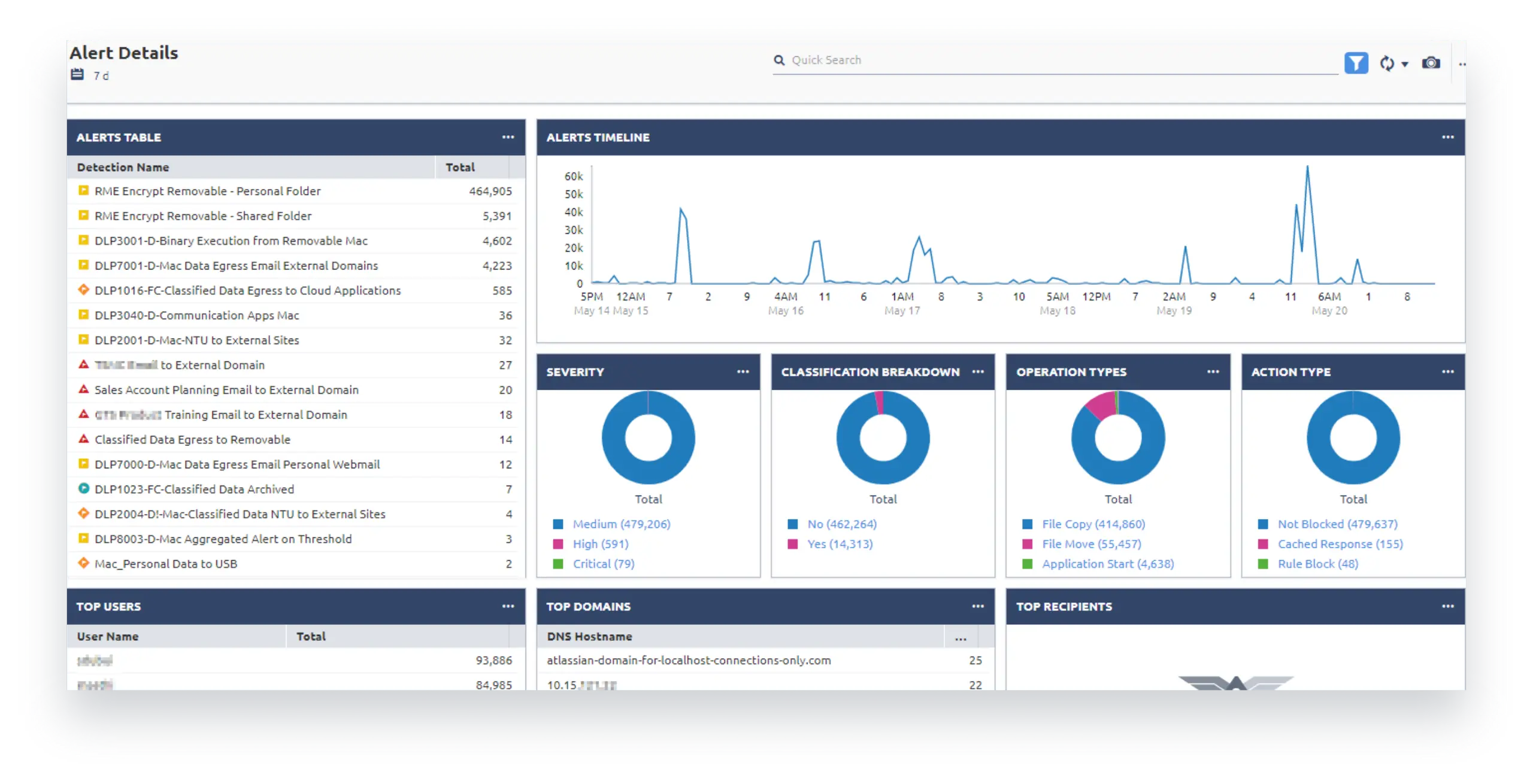
Using a combination of pre-built reports and reports tailored to your business the DG MSP team will show you just how much detail you have, from day one. The DG team will use this to inform you and your leadership team of how and where your sensitive data is moving.
Once you are ready to take more action, our team will discuss with you what actions makes the most sense to prompt end users. Adding these prompts when specific actions occur serves to remind employees of the policies and the importance of safe data handling.
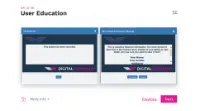
Here’s what an informational prompt looks like and what a justification prompt looks like. We will work with you to customize how they look to meet your needs.
PHASE 5 - CONTINUOUS EFFORT
Controlling Data

During data discovery, if there are key sensitive pools of data that warrant automated blocking we’ll discuss the best options to ensure existing workflows are minimally impacted.
PHASE 5 - CONTINUOUS EFFORT
Controlling Data
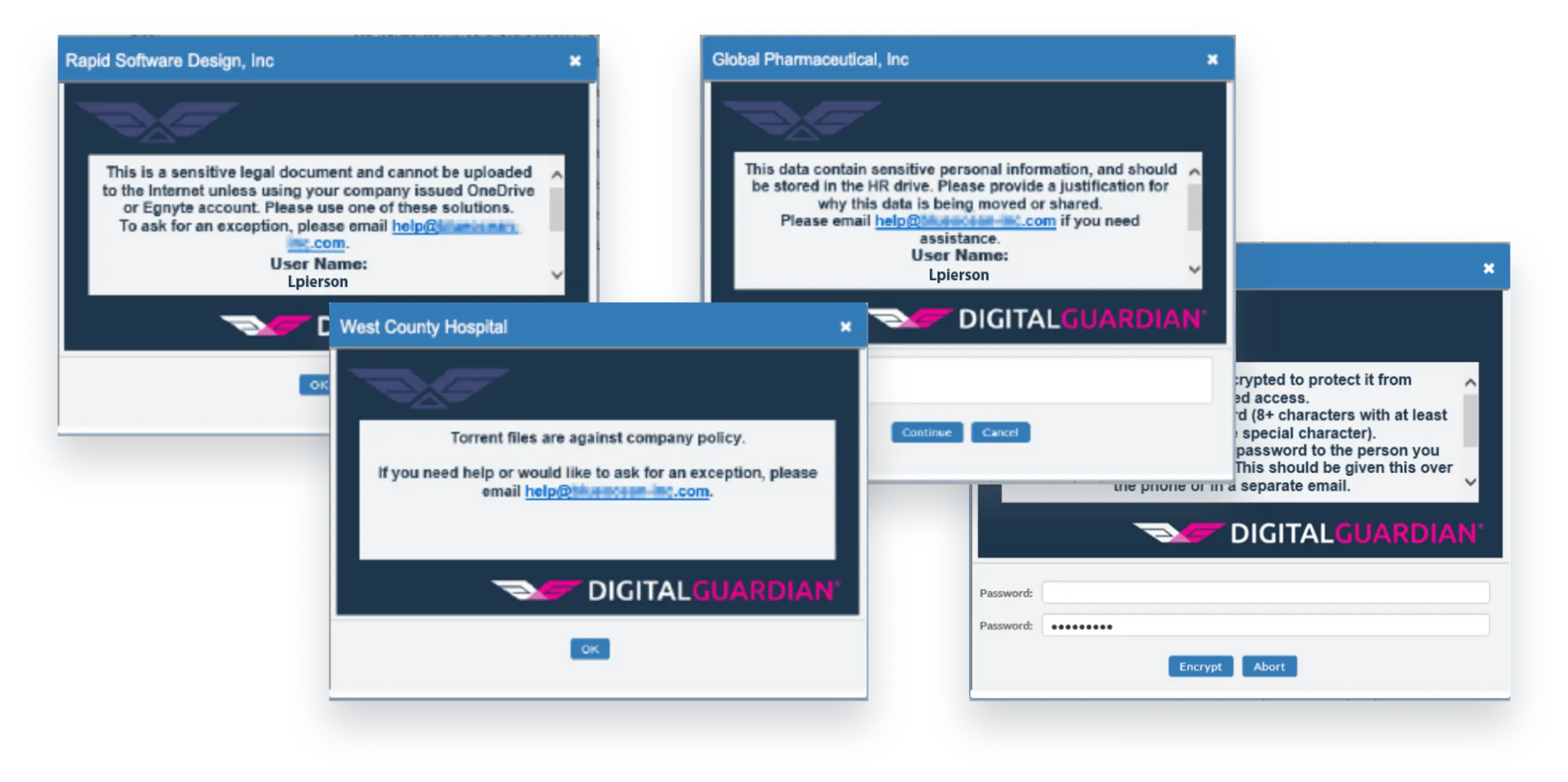
Once you and our team determine any high value data sources that need automated data controls, we’ll customize the prompt. These messages reinforce existing policies, but give users the escalation process if business processes are not in alignment with the data controls.
Making MSP DLP Programmatic for Success
Getting Started
-
Weekly Non-Business Use Reports
- Identify potential employee misconduct -
Monthly Executive/Board Reports
- Identify ongoing data trends in business -
Assessment, Development, Refinement
- Are the rules working, is the business evolving?
Ongoing Cybersecurity Expertise
-
Eyes on Glass for Near Real Time Alerting
- Analysts triage alerts and notify you upon potential data theft activity -
Around the Clock Service and Support
- 7/24/365 access to your support and administration team
Increasing Maturity
-
Incident Response Program
- Collect the forensic artifacts
- Respond and Remediate
- Document & Modify -
Threat Hunting Program
- Dedicate time to proactively hunt throughout your entire extended enterprise
Making DLP an ongoing program is key to success. Our MSP team will provide a cadence of reporting to the business. Our experts are the 24x7 data stewards. We give you near real time alerting required for defend against the global threatscape. We’re here to answer your questions when you need us.
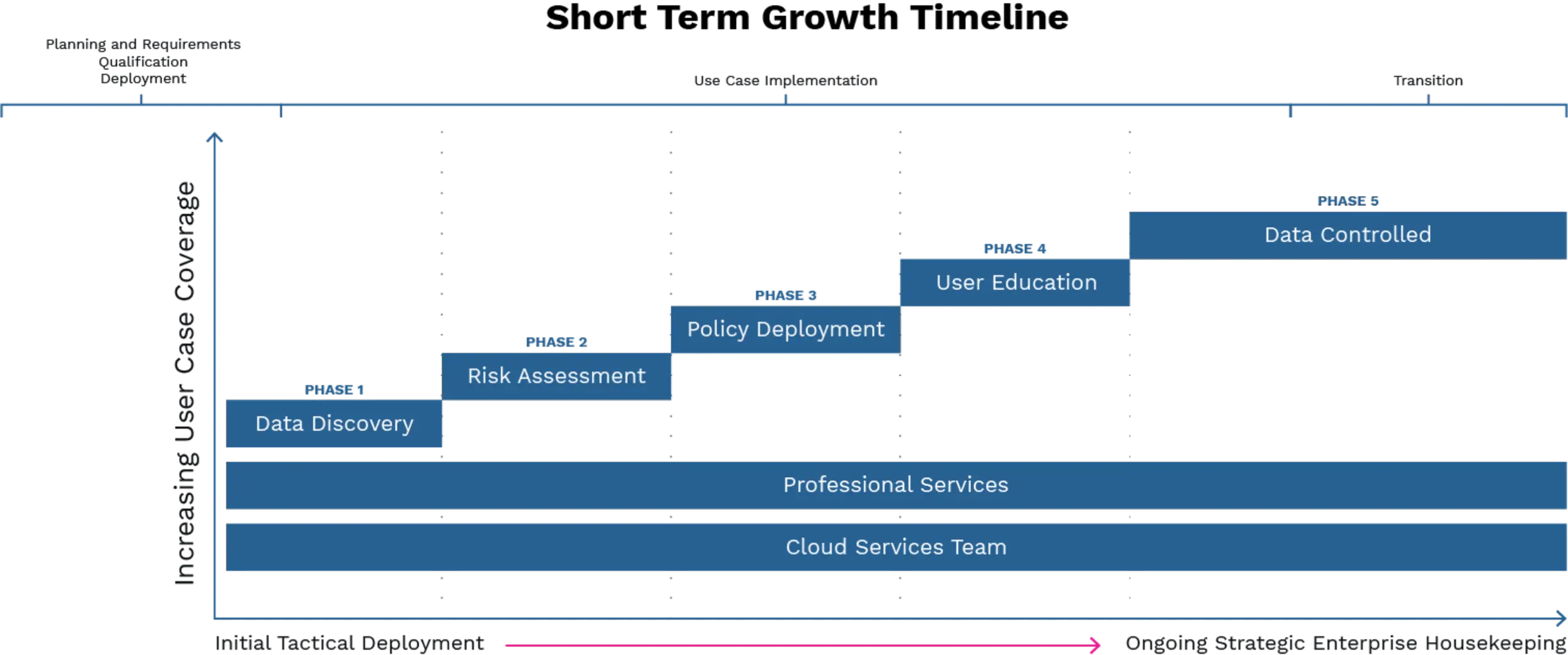
This is your timeline to implementing your data loss prevention program.
PHASE 1
Data Discovery Goals
- Documents the existence, scope, and severity of your data risks.
- Shows complete usage context from executive summaries to detailed forensics.
- Measures effectiveness of your current security policies and technology investments.
- Identifies how you can best take action on potential data threats.

Digital Guardian automatically locates and documents sensitive data in storage, in motion, and as it is created. This first step enables your team to better create policies based on the actual data patterns vs speculation.
PHASE 1
Data Discovery Analytics
On demand and regularly scheduled overviews of activity.
Send Mail | NTU | CD/DVD | Removable | Copy & Paste | Print | Custom

Once you’ve run your data discovery, the detailed reporting let’s your team see what is where, how it is moving, and where you might already have some risks you were unaware of. You can use this as documentation for data protection policies, and a baseline to show improvement.
PHASE 2
Risk Assessment Goals

With the initial data discovery complete (this is an ongoing part of an effective program - data footprints evolve), setting risk assessment goals lets you and the team decide what is acceptable.
Risk can be both good and bad, it is a matter of deciding if it is within the risk threshold of the business. Establishing who on your team does what and the escalation process is critical – do it when there isn’t a potential incident in process.
PHASE 2
Risk Assessment Methodology
Data Classification
- What constitutes sensitive information?
Data and Entity Inventory
- Where is it?
- How much of it is there?
Current Control Review
- How effectively is it protected?
Vulnerability Assessment
- What are the vulnerabilities that could lead to compromise?
- What is the likelihood of compromise?
Data Sensitivity and Risk Tolerance
- What is the potential impact?
Cost Benefit Analysis
- What is the most effective use of protection resources?
Here is a framework to help with your risk assessment. It serves as the basis for what our team uses and starts a discussion internally around what your data protection program should emphasize.
Going from limited visibility to the full visibility DG delivers can illuminate risks that were there all along, seeing them can be eye- opening. Use this starting point to inform the business and then show how your team is using DG to reduce risky behavior over time.
With the knowledge gained during the discovery phase you can deploy better policies the reflect business reality. You can start with alerts to just your team to monitor data movement and further analyze business processes. You can use this to validate or adjust policies as needed.
PHASE 3
Policy Visibility
Incredible insight on day one

With Digital Guardian Analytics & Reporting Cloud the pre-built reports guide you to the information you need regardless of your role. Out of the box your CISO, information security analysts, threat hunters, and incident responders have a place to start.
Next on the alarm escalation level is prompting. Your team can choose which events that generate alerts are worthy of generating prompts. These prompts can inform users of their actions or require a justification to proceed.
Here’s what an informational prompt looks like and what a justification prompt looks like. You can customize how they look to meet your needs.
For organizations that wish to implement active controls, your options include prompt block, silent block, quarantine, and encryption. When you need to err on the side of caution these automated controls stop data loss before it happens.
For any automated data controls, you can customize the message to explain to the users why this action was taken. Reinforcing security policies with these messages supports enhanced data security.
Making SaaS DLP Programmatic for Success
Getting Started
-
Weekly Non-Business Use Reports
- Identify potential employee misconduct -
Monthly Executive/Board Reports
- Identify ongoing data trends in business -
Assessment, Development, Refinement
- Are the rules working, is the business evolving?
Getting Proactive
-
Threat Hunting Program
- Dedicate people and time to proactively hunt throughout your entire extended enterprise
Increasing Maturity
-
Incident Response Program
- Establish and document your IR plan
- Collect the forensic artifacts
- Respond and Remediate
- Document & Modify
Expert Assistance
-
Managed Security Program
- Enlist DG cybersecurity experts to be your cybersecurity experts.
- Fully managed data security to reduce operational overhead and rely on a dedicated team to defend your sensitive data
Making DLP an ongoing program is key to success. Digital Guardian gives the insights into your data movement you need to engage the entire business in a conversation that drives a successful DLP program and secures enterprise growth.