Secure Collaboration
Your data will travel.
Shouldn't your security?
Short on time? View a demo recording
Speeds and secures collaboration on any document.
No software required for end-users — internal or external.
Digital Guardian Secure Collaboration (previously known as Vera) makes it effortless to securely collaborate with anyone, no matter which tools they choose to use.
Digital Guardian Secure Collaboration ensures that your sensitive data remains in your control outside the organization.
Want to learn more, or speak with an expert from our team?
We’d like to hear from you.
What makes your organization unique?
We can protect that advantage.

Learn how we make it effortless to securely collaborate with anyone, on any device with this informative technical whitepaper.
How Multiple Industries Found Success with Digital Guardian Secure Collaboration

Organizations from all shapes and sizes, from manufacturing to healthcare, have found success with Digital Guardian Secure Collaboration. Read through this eBook for 19 success stories describing how the tool has helped them securely share their data and IP.

ENABLE COLLABORATION SAFELY
Documents are encrypted even after download, giving you control inside and outside your environment.

ZERO TRUST FILE SECURITY
Secure sensitive data. With a single click, protect any file type with AES 256-bit encryption.

EASY ADOPTION
No software installation required. No significant workflow changes or training required.
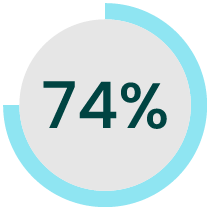
74% of breaches involve the human element.
We give you an "undo" button.
Source: Verizon 2023 Data Breach Investigations Report
DATA TYPES WE PROTECT

Financial and Legal Documents
Easily and securely share financial and legal data with third parties external to your organization.

Files in Cloud Collaboration
We automatically protect your sensitive content no matter where you store it, including Box, DropBox, OneDrive, SharePoint, or on-premises.

Manufacturing CAD/CAM Files
Keep trade secrets secure, from R&D and product designs to supplier contracts.

Secure Any Data or File Type
Our platform is content-agnostic, so we can secure any type of file, from board communications to sensitive HR documents.

How Does Digital Guardian Secure Collaboration Work?
- Protects any file type, on any device, with AES 256-bit encryption
- Digital Guardian Secure Collaboration (formerly Vera) seamlessly integrates into cloud storage platforms without impacting the user experience
- Automatically secures data uploaded into specific cloud storage folders, or protects entire accounts
- Tracks where files are opened in real-time, even if they're downloaded, copied, or moved into an untrusted sharing service
- Enables dynamic changing of permissions and access to data, regardless of how or when it's shared
- Allows you to instantly revoke access from any user, device, or organization
- Seamlessly maps complex permissions to cloud security groups

